Your Modern Workspace
We provide businesses with a digital workspace based on Microsoft technology. You benefit from our outstanding technical expertise and unmatched excellence in customer support.

How Are We Different
We maintain a big-picture view in strategic planning, continuously develop our team's technical expertise, and strive to provide the best-in-class support to our customers.

We conduct monthly digital transformation calls with our customers to properly understand their objectives and ensure the projects have proper focus and priority.

Our experts have worked with Microsoft Cloud since its very early days and have accumulated a wide range of expertise to make our projects successful and delivered on time.

Customers contact our support via email, phone, and other channels to receive quick responses to their questions and prompt resolutions to their technical issues.
Our Proven Track Record
Over the years, we have successfully served hundreds of clients across the globe.
25
Years in Business
18
Years as Gold Partner
5
Global Office Locations
28
Countries Covered
5,620
Clients Served
1,160
Clients Under Management
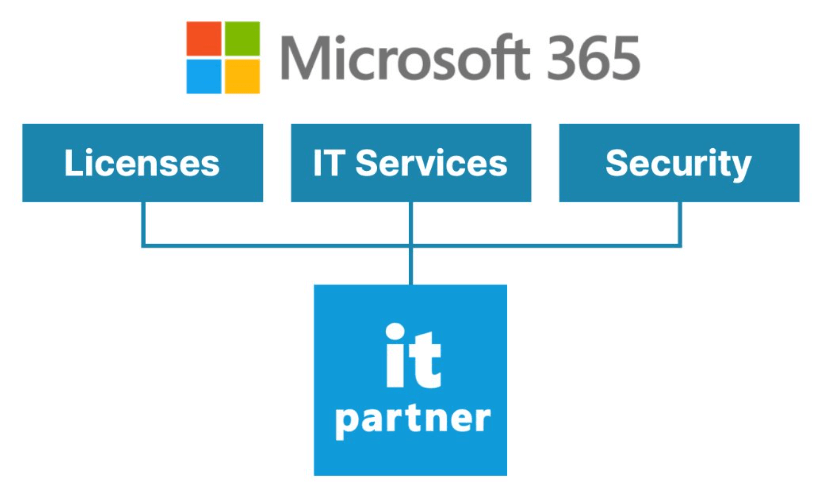
The End-to-End Solution
Our offering encompasses every aspect of your Microsoft365 workspace. This includes not only the licenses for all necessary products but also dedicated IT services for seamless implementation and ongoing support, coupled with robust security measures to safeguard your data.
Our Happy Clients
We support businesses across many industries, including finance, insurance, healthcare, pharma, technology, engineering, transportation, hospitality, entertainment, legal, government, and military.

IT Services - What We Do
We provide a comprehensive suite of services from initial assessment to migration, implementation, custom development, managed services, and support services.

We conduct workshops and audits of your current infrastructure and develop recommendations.

We migrate your workspace to Microsoft Cloud from on-premises, third-party cloud (Google), and tenant-to-tenant.

We configure your digital workspace and onboard users into their new modern work environment.

We create process automations for your business using SharePoint 365 tools and Azure App Service.
We monitor and manage your environment proactively to assure high performance and availability.

We answer user questions and resolve issues to enable the highest possible productivity of the customer’s team.
Migration - What We Do
We facilitate a seamless transition of your workspace, applications, and data to the Microsoft Cloud, ensuring a smooth migration from on-premises infrastructures, alternative cloud services, or between different Microsoft tenancies (tenant-to-tenant migrations)."

We transfer your data and email from Google Workspace to Microsoft 365 quickly and with minimum impact to your users.

We migrate your Exchange, SharePoint, File Servers, Windows, and SQL Server to Microsoft 365 and Azure.

We move your data and email within Microsoft 365 to another tenant using automated data discovery and proven process.

Beth Tippett, Director of Information Systems
IT Partner was engaged to synchronize Active Directory with Office 365. I was very satisfied with the services they provided. With their expertise, they could complete the project without impacting our users. I found the IT Partner team very knowledgeable, prompt, accessible, and easy to work with.

Alex Leblois, President and Executive Director
G3ict engaged IT Partner to migrate its websites from a legacy platform to Azure and its entire office and email exchange to Office 365. From the first day, the IT Partner team demonstrated incredible commitment to making things work. The support we received post-migration was always prompt, professionally handled, knowledgeable, and effective. We could not be happier.

Romain Raye, Sales Director
Right after the first meeting, we chose IT Partner. These guys answered all our questions, presented a migration plan, and immediately got to work. They migrated our email system and existing email data from the old public service to Office 365. The IT Partner team is client-oriented and has exceptionally high standards in customer service. They are pros, and they know what they are doing.

Roland Shafer Jr, ICT Director
IT Partner team was extremely helpful in moving our non-profit organization into the Office365 environment we are now using. We are so thankful for the kindness and effort of IT Partners in helping us meet our deadline. All in all, our project went well.
Security - What We Do
We take complete responsibility for planning, implementing, and managing the security of your workspace, devices, and cloud infrastructure.

We audit your environment and identify priority enhancements needed to increase your Microsoft security score.

We configure security tools to monitor and protect your workspace, devices, and your cloud infrastructure.

We monitor and provide incident response to prevent intrusion and loss of your private data.
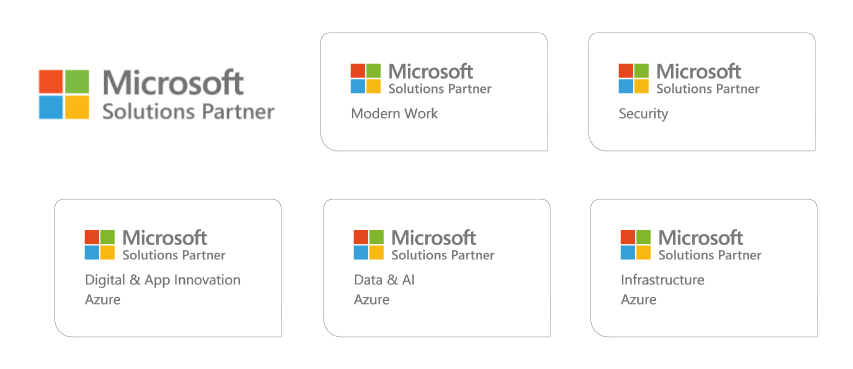
A Gold Microsoft Partner Since 2006
We bring over 18 years of experience as a Microsoft Gold Partner. Our engineers are certified in Modern Work, Security, Infrastructure, Data & AI, and Digital & App Innovation.
We Are Happy To Help
Contact us for more information, request a quote, or get expert advice.