Worldwide Government Security
#advanced threat protection, #modern security, #office 365 compliance
Government agencies work hard to deliver value to society. As modern technology shifts societal behavior, citizens expect their governments to adapt accordingly. The reality today is that confidence and trust in governments throughout much of the world are consistently low and constantly being challenged. Public officials have additional pressure now to double down on their good stewardship of sensitive information, but they are also required to do more with a smaller budget, which can be a hurdle to delivering on these commitments.
At the same time, governments face a growing number of threats from increasingly sophisticated cyberattacks that often outpace IT resources. And while external actors account for most of the breaches, malicious intent or accidental error by insiders also account for the loss or exposure of sensitive information. Additionally, the number of regulations, policies, and procedures that must be met is growing year after year. But reactive spending on security because of tight budgets leaves agencies with trailing technology and systems that are older and more vulnerable.
Successful governments around the world are embracing digital transformation to spur innovation, enhance services, improve their critical infrastructure, better engage with citizens, deliver trust in elections, and create smart cities. All of this requires communication across departments, agencies, and jurisdictions to deliver on those missions. There is increased reliance on cloud and mobile, AI, and IoT technology to meet rising citizen expectations with simple and efficient solutions. With that, the amount of data being collected, used, and shared is growing exponentially. As this information flows more freely across these channels, exposure increases and there may be unintended consequences. As this exposure increases, executives across government organizations should work together to ensure the safety and integrity of their organizations' data.
Microsoft 365 solutions address the needs of a modern government by empowering employees to collaborate securely and productively. Microsoft offers end-to-end, intelligent security solutions to help agencies ensure that the right people have access to the right information, to help protect against cyberattacks and to reduce compliance risk.
Citizens expect their government to do more and move faster while being more transparent about how they are protecting public data. Delivering on that requires continued communication and collaboration across government entities, as well as increased reliance on cloud and mobile technology.
But as the digital landscape grows, government agencies face increasing risk from external cyberattackers, accidental or malicious leaks from internal users, and a growing number of regulatory compliance requirements to meet.
Delivering better services and increasing citizen confidence means that your employees will need to be more reliant on technology to be productive from anywhere on any device. To keep missions moving forward, employees today need to be able to access government resources and applications from many locations and devices -- including personally owned devices. Providing extra verification (also referred to as MFA, or multi-factor authentication) is easy and painless, but also protects the company. If your password is compromised, a would-be attacker will still need your phone in order to access the files.
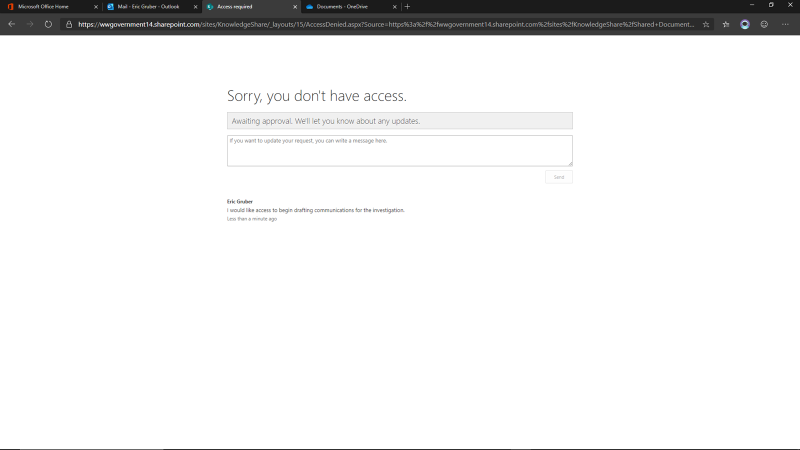
Many government documents require different levels of security classification. Ensuring that the right people have the right access to the right information requires controls so they are granted access only to resources that are necessary for their role or security clearance. Conditional access policies enable your IT team to assess risk in nearly real-time and allow dynamic access to resources as roles and responsibilities -- or conditions -- change. This proactive control can help you ensure users do not have blanket access to agency resources.
You can also download the Outlook mobile app and configure your work email account using MFA on your phone to verify your identity. If your organization uses Microsoft Intune to manage mobile devices and mobile apps, you can install a government application on your personal phone, enabling you to be efficient while away from the office. You have permission to read the confidential document but can't save it to your phone. Your agency can help protect access to sensitive data on personal devices by restricting actions users can take, such as copy-paste, save, and view.

Implementing policies and programs rarely happens in isolation. Employees need to exchange information to collaborate and innovate on mission objectives. However, as data is shared, vulnerabilities increase. Microsoft 365 helps you securely share information while reducing the risk of accidental or intentional leaks.
The release contains information about the incident that is still not ready for the general public. You can easily attach the document, then encrypt the entire email with a single click. This encryption ensures that the email is only readable from the inbox of the direct recipients and that the attachment is also encrypted. If this document is downloaded and copied to a USB drive or to an untrusted device, the document will remain protected. The encryption will also prevent the recipients from forwarding the email. This applies to both internal and external recipients. This built-in encryption helps government agencies remain compliant by preventing intentional or accidental sharing of emails and information. Encrypted messages can be set to expire or revoked as needed. And these encryption actions are logged and auditable to help meet compliance obligations.
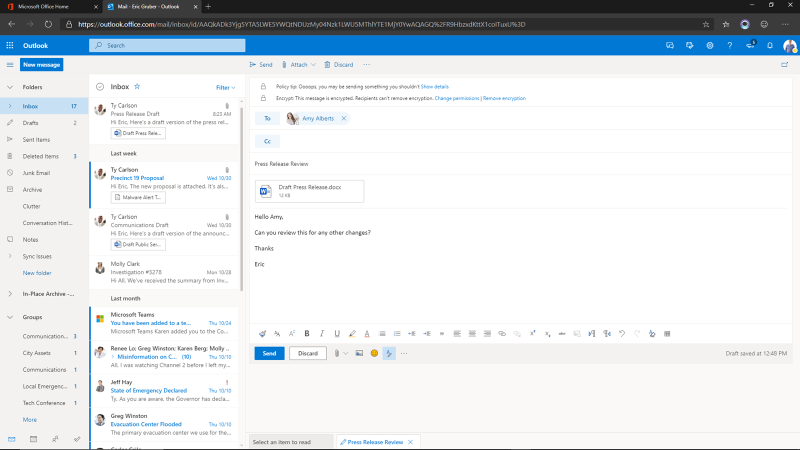
The agency can configure policies to automatically classify, label, and protect data based on its sensitivity. In this case, along with the classification label, the document is also automatically protected with rights-based permissions. So even if someone has accidentally sent this to the press, the receiver would not be able to view the content, saving the agency from becoming an accidental headline.
Data protection can also be managed if documents like this are uploaded to a third-party app using Microsoft Cloud App Security, our Cloud Access Security Broker offering.
Microsoft 365 information protection solutions help ensure that important information is only accessible by those who are authorized to receive and view the information and that critical data is not accidentally released or deleted. Policies can be customized and leveraged to automatically secure data according to compliance laws. Policies can be applied across Microsoft 365, Teams, Exchange Online, and SharePoint.
Protecting users from cyber-threats
Microsoft Threat Protection is built to protect the modern institution from sophisticated cyber-threats by offering comprehensive, advanced, and integrated security across multiple attack vectors. Fake, phishing emails are difficult for most users to recognize when the links and attachments are constructed to look legitimate. In addition to solid user education, services to stop these attempts before the user can interact with the malicious content are important steps in preventing these attacks from being successful.
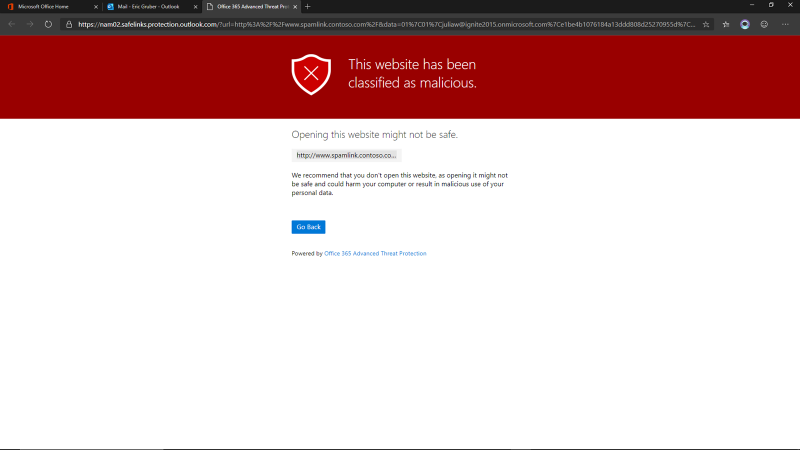
ATP Safe Links opens and detonates the link in a secured session to check for malicious content. It finds malicious content in the link and gives you a warning notification that the link was in fact malicious. This helps prevent malicious content, such as ransomware, from being downloaded on your computer, thus proactively preventing a data breach or credential harvest and helping to save the agency from a potentially damaging and expensive breach.
Advanced automation powered by artificial intelligence (AI) to enhance incident identification and response enables security teams to resolve threats accurately, efficiently, and promptly. Machine learning also enables us to link together individual signals, then correlate related events to provide important context.
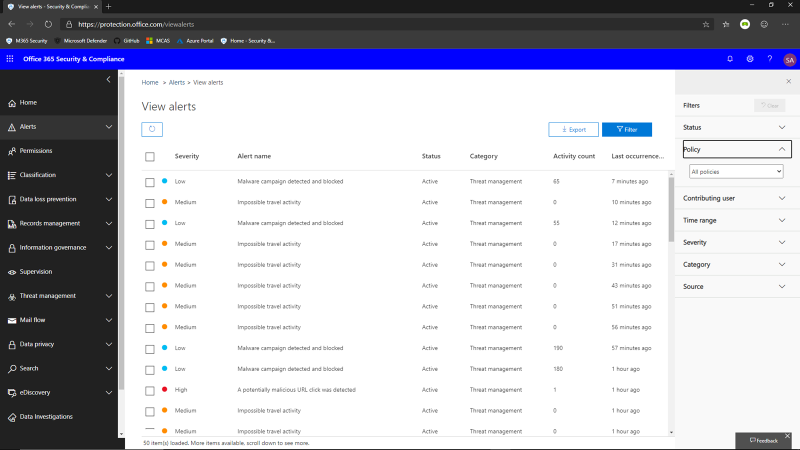
Should an attack happen, Microsoft Threat Protection automatically acts to keep the users and the entire organization safe. The emails containing the malicious links are soft-deleted. This means the links have been removed and depending on the amount of malicious content in the message, the message will be removed and placed in quarantine.
Any users who managed to click the link before neutralization will have been
recorded. This allows the admins to target education for these users.
Automated incident response can help mitigate more threats in real time,
improving the efficiency and overall security for the organization. It
contributes to lower costs for managing information security.
As the digital landscape changes, government organizations have an opportunity to enhance services, modernize the workplace, and improve engagement with citizens, all while remaining trusted stewards of sensitive data. To address the growing number of sophisticated threats and compliance requirements, Microsoft 365 offers a breadth of tools and services that allow governments to keep their data secure, compliant, and accessible.
Share
2020-05-06