Managing data risk in the post-GDPR (General Data Protection Regulation) world
In the middle of May 2019, a compliance and security conference took place and, in case you missed it, we’ve prepared the recap of some sessions for you. One of the presentations was hosted by Silvia Kingsmill, a partner in a risk consulting practice at KPMG Canada, and a National Data Protection and Privacy Leader (yes, you’re not mistaken, the very same KPMG from the Big Four accounting firms). This session was devoted to an overview of the regulatory landscape. She spoke about data privacy, cyber security, data governance, digital transformation, and what’s more important, offered advice on how to reach compliance and improve the security posture of an organization.
According to Silvia, data is the #1 strategically important asset; it is the new oil of the digital economy. It enables us to give a better customer experience, and transforms the way we work, live, play, and interact with one another via social media channels. It gives every organization the ability to drive insights into the customer experience to deliver better products and services and transform industries. However, all of this doesn't come without risk. Data needs to be managed, used responsibly, ethically, and there need to be accountability measures in place. So, let's discover some of the challenges and operational pitfalls that KPMG observes with data risk management in the post-GDPR world.
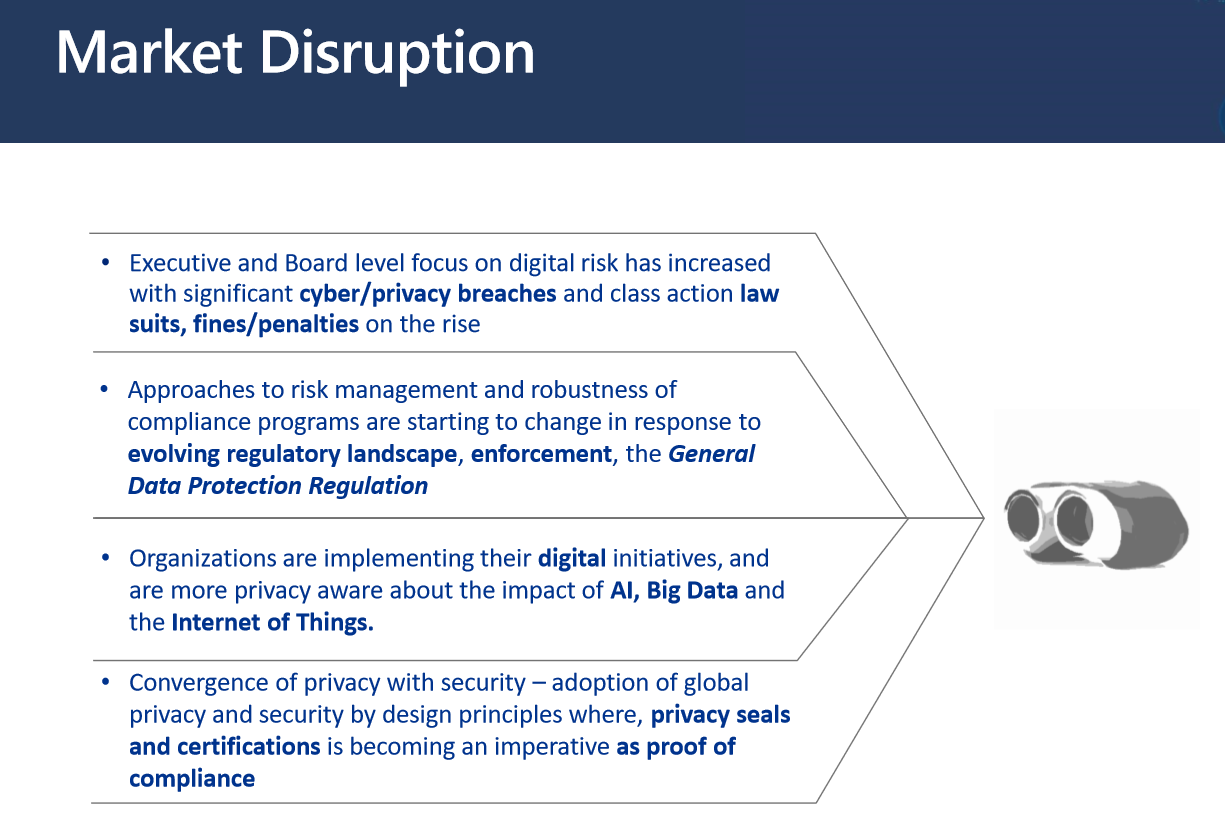
Drivers of market disruption
KPMG defines four drivers of change responsible for market disruption, the first of which is massive cyber and privacy breaches, which have resulted in class action lawsuits, extensive fines, penalties, and regulatory scrutiny.
Regulatory landscape is the second driver of change. GDPR, or General Data Protection Regulation, for example, imposes extreme fines and penalties for non-compliance. It requires organizations to think differently about privacy risk management and the robustness of their existing compliance programs.
The third driver of change is emerging technology. This includes digital transformation influenced by artificial intelligence, big data, and the Internet of things. Organizations are becoming more privacy aware, and more sensitive to the impact these emerging technologies have on customers. There is a big trend in the industry; going over and above regulation, where industry organizations are getting together to develop industry standards for certification purposes (like the CIO Strategy Council, the International Organization for Standardization, and others). It enables emerging technologies to be rolled out safely, in an ethical and trustworthy manner.
The fourth driver of change is the need for proof of compliance. It's no longer enough to say we're "doing" privacy, and we're "thinking about" cybersecurity and risk management. Organizations are required to be accountable for their information handling practices, and they need to operationally track and demonstrate due diligence. So, there's another trend in the marketplace for privacy certification schemes and global certifications against ISO standards, like privacy by design, for example. This KPMG expert expects that in 2 or 3 years, we'll see the evolution of ISO standards for privacy by design for consumer business services.
GDPR and its global impact
Buzz words we hear all the time are accountability, responsibility, transparency, ethics, and trust. Organizations are in the business of trust, and the EU's GDPR raises the bar of the data protection standard. GDPR became the game changer in terms of citizens' rights, as it standardized and harmonized the rules across EU states and let citizens challenge the companies if they use their data without consent, transparency, and accountability. And it is also a game changer for the supply chain, as data processors and data controllers collecting information at first instances are equally responsible for data protection. To learn more about GDPR, please see here .

Governments around the world are enacting similar GDPR-like legislation.
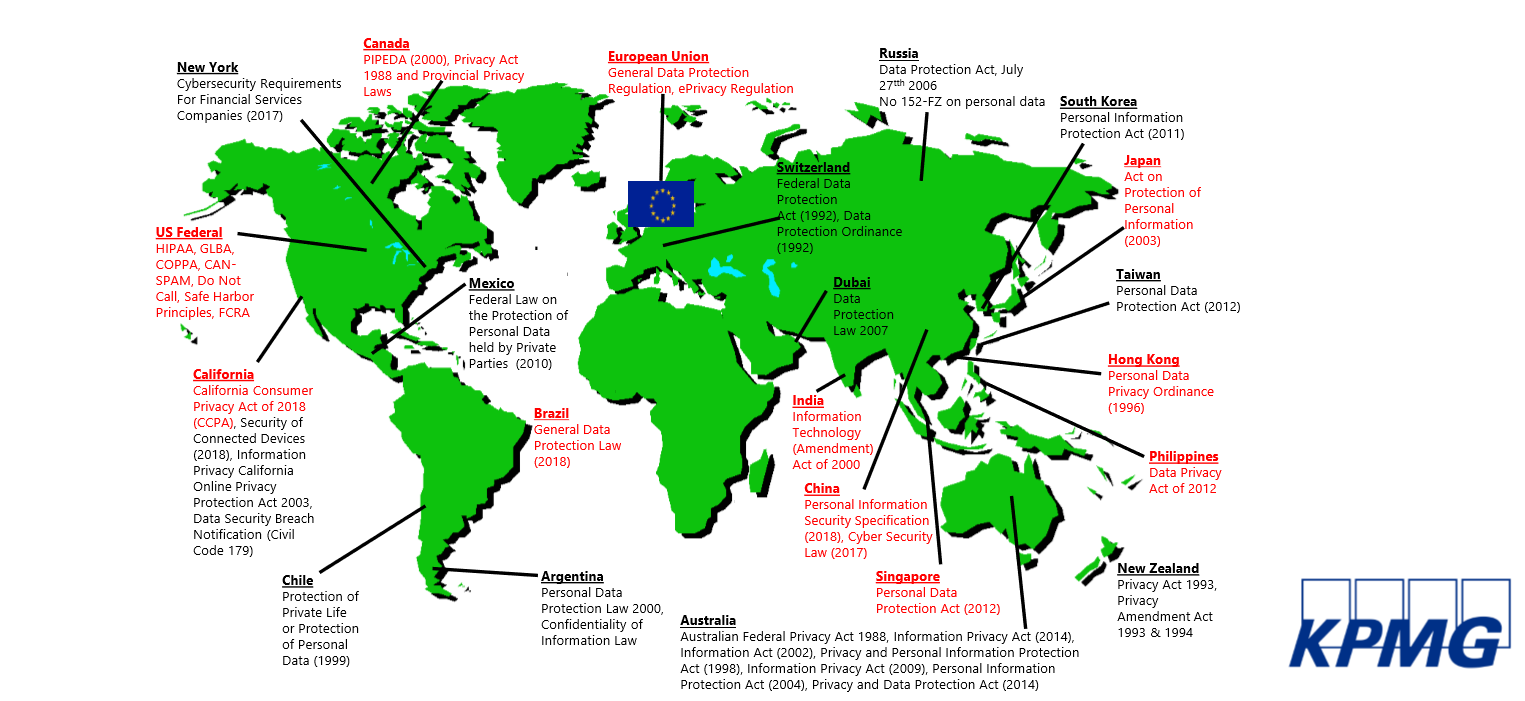
In the absence of legislation, regulatory guidance that mirrors the language of the GDPR has been issued by different data protection commissioners around the world. Silvia Kingsmill predicts global changes that will line up to the expectations around data protection under the GDPR.
There is also a philosophical shift and organizational commitment to privacy, which is about proactive risk management and a movement away from a tick-the-box compliance exercise to the exercise that looks to remediate the highest risk when it comes to information and data management.
Privacy by design
Leading-edge companies and regulators are committing to privacy by design. It is the philosophy of embedding privacy and security into the system design and architecture of any emerging technology, into day-to-day business practices, and into the organizational culture, making sure that you proactively manage the risk up front and not retrofit your systems. In fact, KPMG has developed a privacy by design risk assessment framework that falls under a "comply once, attest to many" (standards) approach.
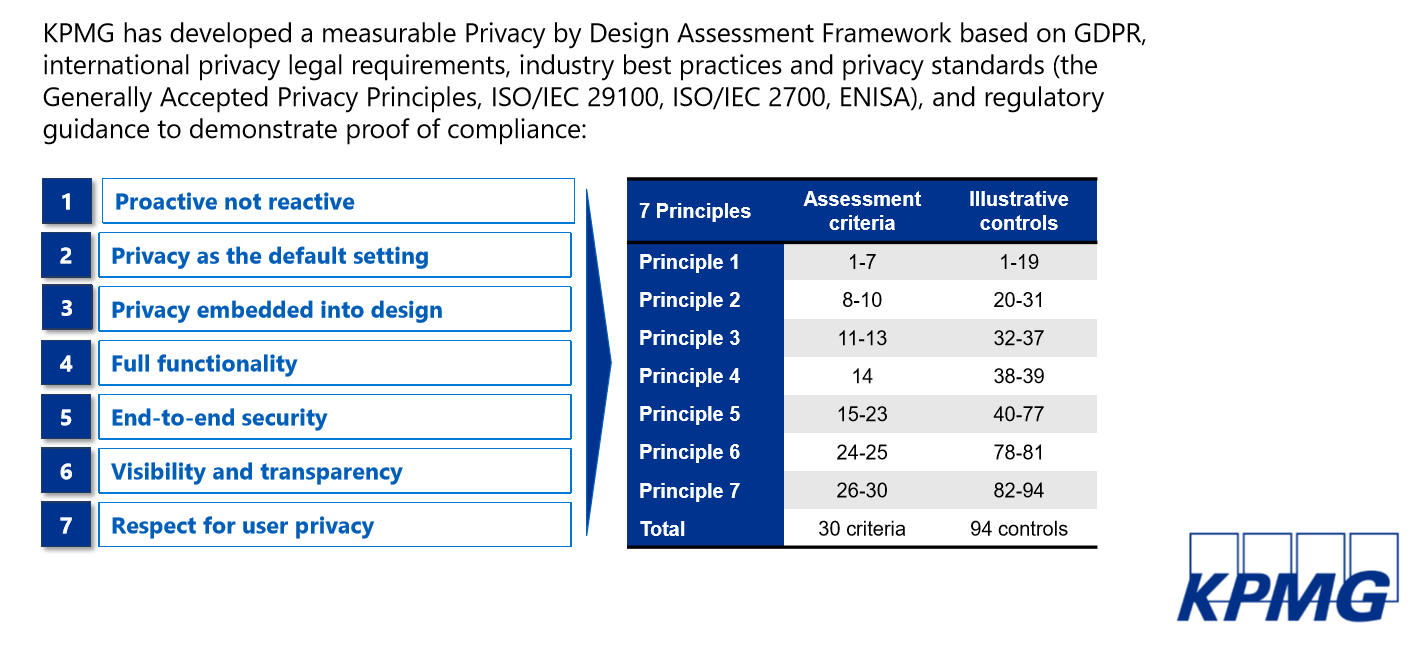
If you want to learn more about your compliance posture against different regulations, check out the tool Compliance manager .
Operational challenges
Companies and organizations are left on their own while implementing some of the new standards and regulations we are seeing in the world of AI, privacy, cybersecurity, and risk management. By KPMG's observations, it's most often the simple things that get companies into trouble with privacy violations, and the reason for most of them is a disconnection between people, processes, governance, and technology. Some of the findings KPMG has in their privacy risk assessment reports are around the over-collection of data, and as a result, the over-retention of it, which increases your privacy risk exposures and your attack surface.
Another way that companies get into trouble is the lack of transparency in the legal language and poorly written privacy policies. According to the regulations, it is expected that companies have accurate and user-friendly privacy policies enabling the customer to understand what information is collected, for what purpose, how it's going to be protected -- and if it's ever going to be shared with third parties, consent will be requested. Monetization of data is also prohibited if it's not done responsibly and ethically. Leveraging insights from the data an organization has about its customer is completely acceptable if it relies on consent, is done in conjunction with transparent policies and procedures, and enables an individual to withdraw consent and to challenge the privacy practices of an organization.
The biggest way companies get into trouble is by ignoring regulatory expectations. Regulatory guidance is more instructive and more important to take note of, as it is what a regulator will look for if you are involved in a privacy investigation or breach complaint.

Digital gets personal
As organizations are in the business of trust, the competitive differentiator will be the capability of organizations to respect consumer privacy and show transparency around information handling. It's all about managing expectations, whether it be from a customer, from a government or legislator, or from regulators.
KPMG is seeing privacy programs evolving where cybersecurity is part of a privacy equation. Organizations are elaborating on their privacy and security programs enterprise-wide to embed privacy into corporate processes and technology decisions, such as in strategic business planning, project management lifecycle, and enterprise risk reporting.
There's greater awareness around privacy breaches and as a result, organizations have become more sensitive to it. They are making pledges to their customers through certification mechanisms to ensure that they continue to earn and keep their customers' trust and manage their expectations in line with privacy and security best practices.
KPMG has conducted several global surveys, interviewing 1,700 CEOs. The results proved that digital is getting personal. It means that protecting customers' data is no longer just a part of corporate social responsibility, it's about doing the right thing. There's a mind shift that implies seeing data, privacy, security, and risk management as opportunities for the organization to build privacy and security figures into their day-to-day business operations and transformation. For more numbers, see the image below.

Some industry trends
It's a myth to say that privacy is only about the B2C environment. B2B organizations are equally interested in privacy rules because they deal with B2C-focused companies that want sufficient guarantees around the privacy protections that are embedded across the supply chain. Contracts are only as good, like paper, as they are written on, if the vendors don't live up to the commitments they make in their privacy policies and in the contracts between the data giver and the data taker.
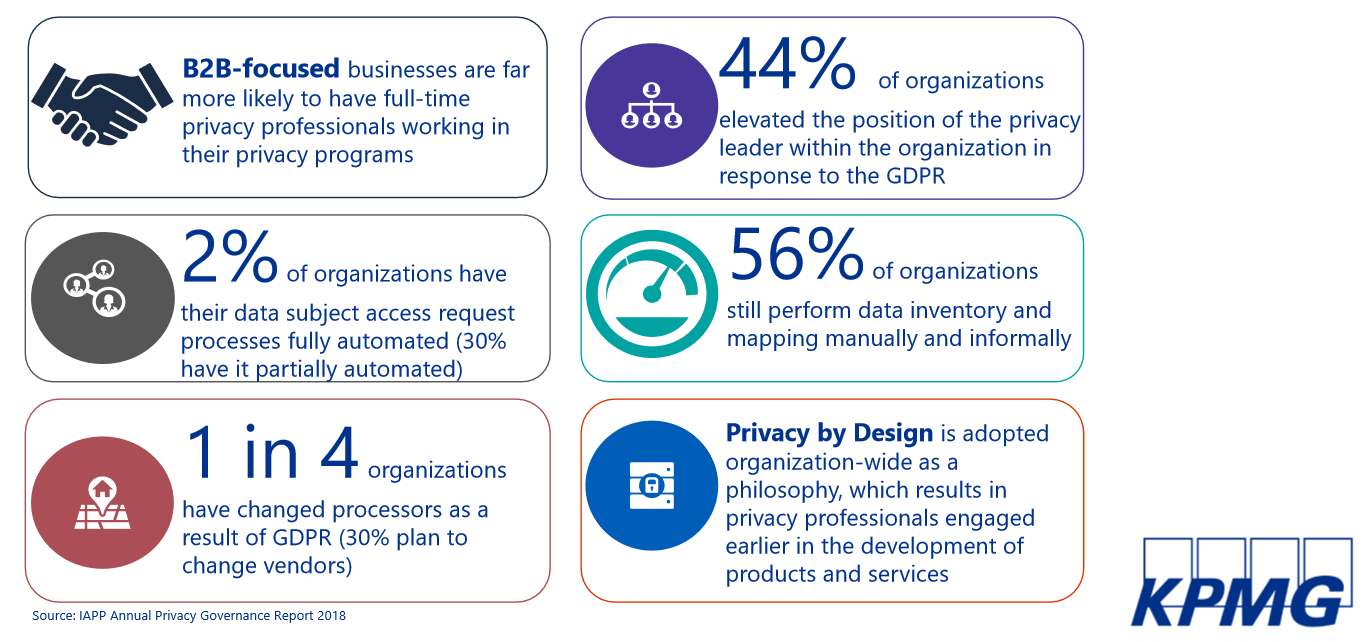
A shift to privacy-by-design thinking around the release of products and services shows that companies are more concerned with the question of what should we be doing with our data to continue innovating and to preserve the trust of our customers, which must be balanced with the regulatory framework around the responsible use of data.
Data mapping has been a cybersecurity practice for many years, and now it's required under the GDPR as law. It means that you need to understand where your data assets live in order to protect them. More mature organizations are trending to automation (instead of Excel sheets) for data mapping.
Under the GDPR, a data protection officer role must be designated under certain circumstances, but more and more companies are doing so as a best practice. These employees are required to develop, monitor, and sustain the privacy program.
Compliance is a team effort
Data protection and privacy are the responsibility of not only a compliance officer but also legal, business/data analytics and technology, and infosec teams alongside the internal audit team.
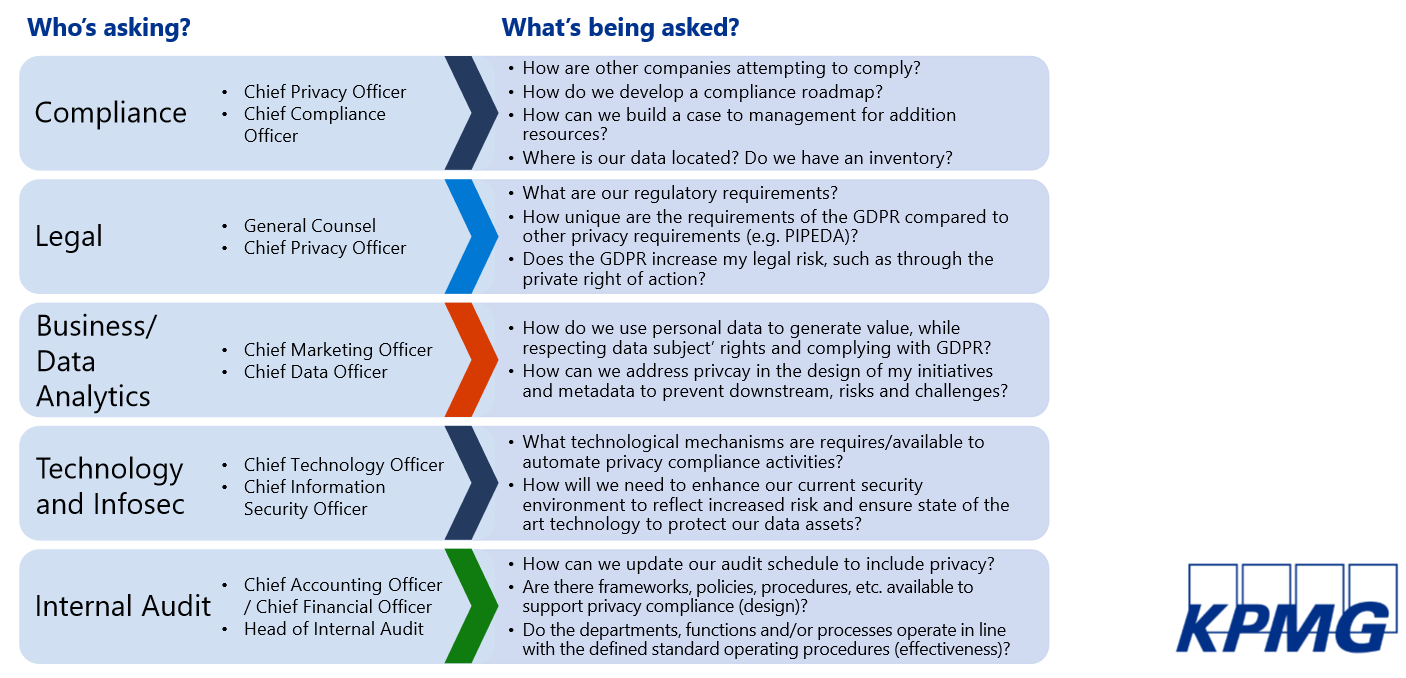
Compliance is not a destination, it's a journey. On the way, you may go through the following stages:
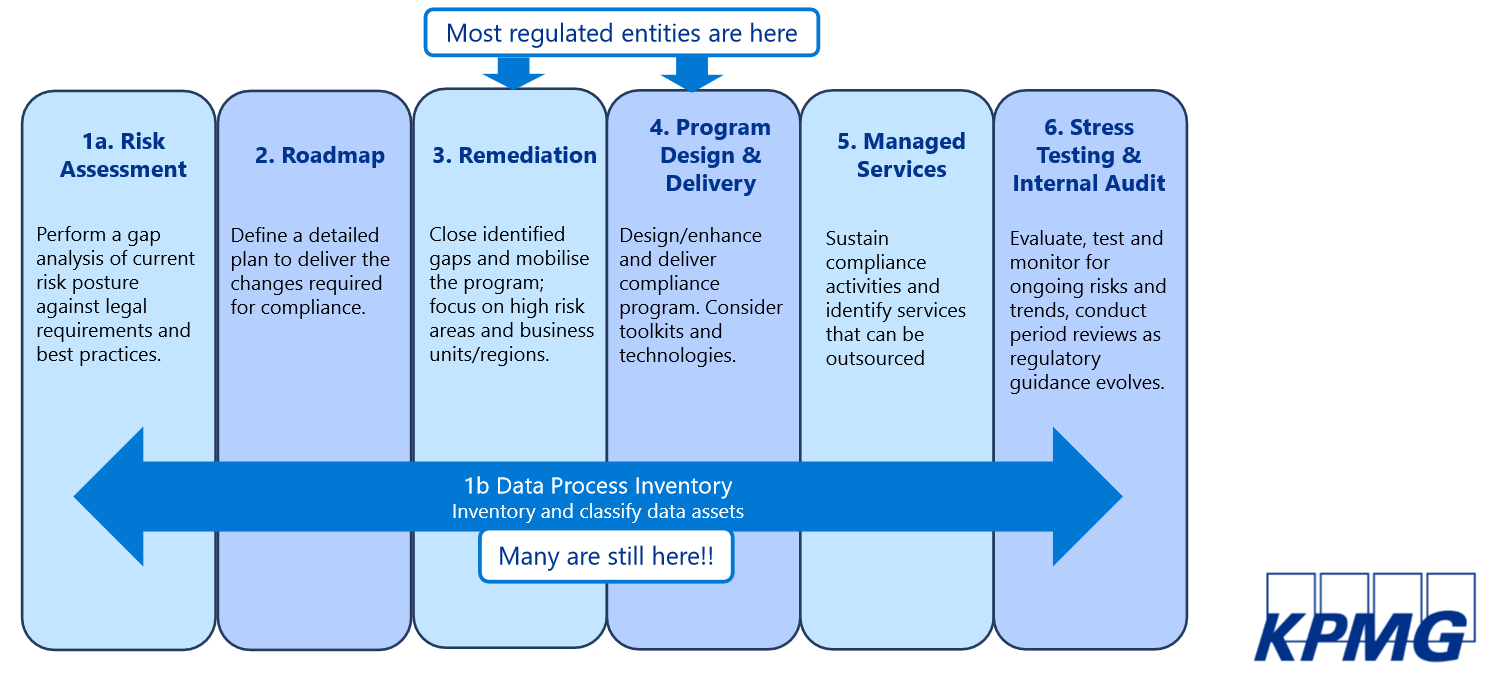
It's important to note that many organizations, irrespective of sector or industry, are still trying to figure out their data process inventory and identify where their most critical data assets live (what server, what application) in order to be able to safeguard the information and understand which third parties or others have access to the information, and ensure there is no inappropriate data access resulting in risk exposures.
If your company is also concerned with the inventory and classification of data assets and you want to follow the trend of automating these processes, you can count on IT Partner's GDPR data discovery Service .
All the different components of the compliance journey can be used together as a good due diligence defense should a regulator come knocking on your door in the event of a privacy complaint or privacy cyber breach investigation. In fact, it can also be used to lessen the severity of fine or a penalty.
Conclusion
A holistic risk management program, when it comes to privacy and security, has several building blocks to it. It starts with a sound business strategy that incorporates data protection, privacy, and cybersecurity. It also involves privacy-by-design thinking and proactive risk management practices that include privacy policies and procedures, and a sustainable target operating model (TOM). Don't forget about training and awareness, because people are often the weakest link. A good program requires good metrics, risk reporting, and evaluation of the entire program end to end, as well as stress testing and incident response policies and procedures.
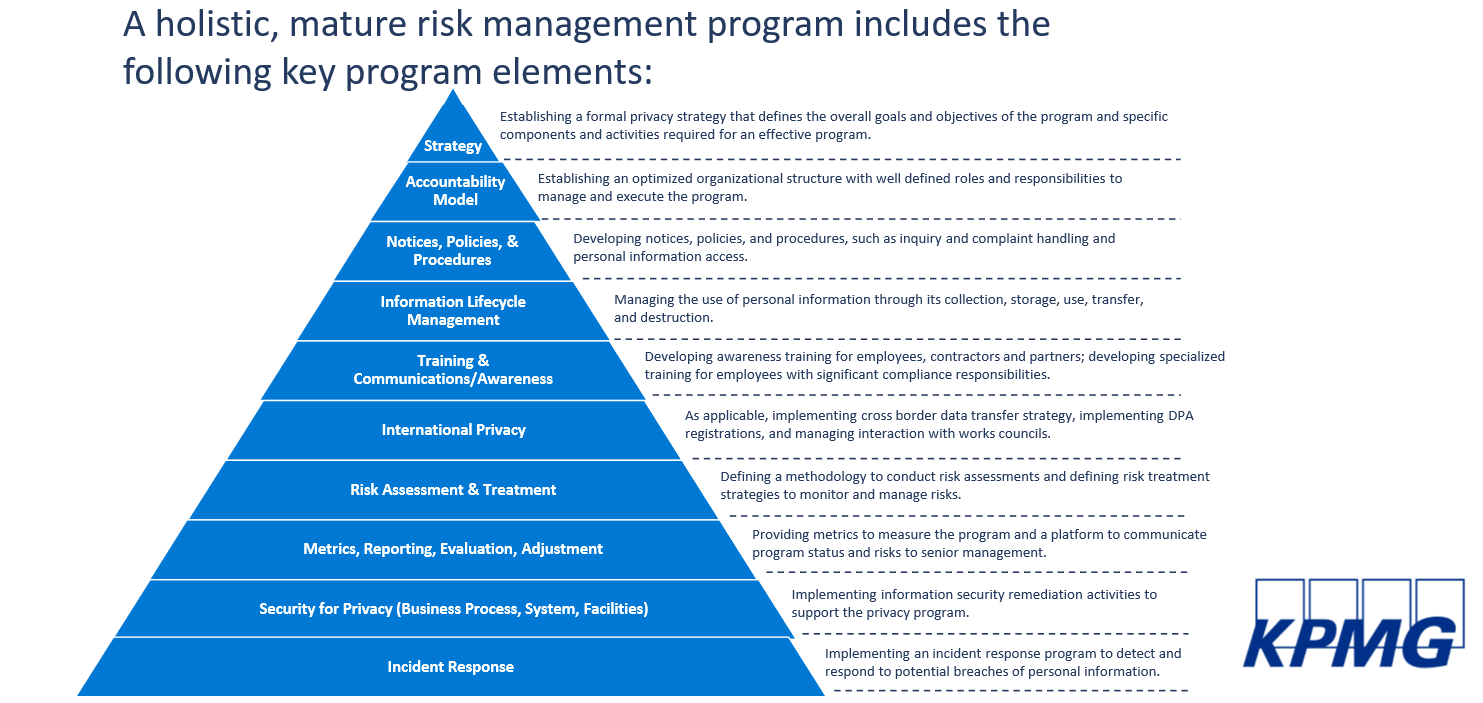
Measuring your risk posture presumes to understand which practices are effective and which are useless. To find your effective practices, KPMG advises to set the position of a fully dedicated chief privacy officer (CPO) or data protection officer (DPO) that has the full backing of the Board and TOM from the top.
Keeping up with privacy-by-design thinking requires training of personnel and stress testing of policies and procedures. Don't neglect stress testing, it is critical, as monitoring and evaluating the effectiveness of the entire program is one of the success factors.
Trustworthy companies are required to have a well-written and fully documented defensible position in the event of a regulatory challenge. Nothing is foolproof, as hackers are always ten steps ahead. Turning compliance into a competitive advantage and market differentiator means being proactive about your risks and embedding privacy and security up front.
Share
2019-06-06