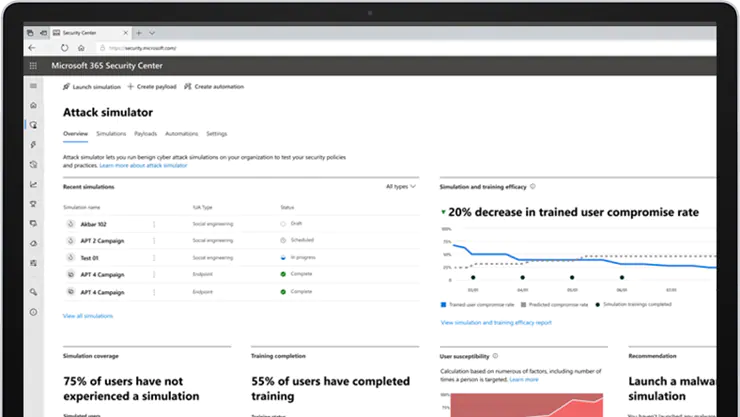
Train your users against cyber-attacks with Attack simulation training
#microsoft 365, #modern security, #security, #cloud security
Cyber-attacks have become the new daily reality for organizations now that most of them have shifted to a hybrid working model. Cyber-attacks can cause major damage to businesses and their IT infrastructure and especially they aim to attack small and medium-sized companies. It is always better to prevent future attacks as it may be impossible to recover from them without the budget or resources to do so.
It is essential to regularly test your security design and implementation to make sure the security assurances are maintained as per the security standards set by the organization. We strongly recommend that you invest in simulated attacks as tests that can indicate gaps. Azure security simulated tests like Penetration testing and Attack simulation training (formerly known as Office 365 Attack Simulator) will help you detect risks early and plan risk mitigation.
What is Penetration Testing (Pentesting)?
Microsoft follows the Assume Breach methodology, where the goal of security is to close gaps in any of the following capabilities:
- Attack discovery.
- Rapid response to attacks.
- Recovery after compromise.
- Preventing future attacks.
One of the benefits of using Azure for application testing and deployment is that you can quickly get environments created. Pentesting is a popular methodology to validate the security defense of a system that allows you to find security gaps by gathering information, analyzing vulnerabilities, and reporting. Once security weaknesses have been identified, they can be prioritized and addressed in order of urgency.
What is Attack Simulation Training?
Attack simulation training, is a tool built by Microsoft to help you detect vulnerable users before a real attack impacts your bottom line and run realistic attack scenarios in your organization. The attack simulation tool mimics real-world phishing and other malicious attacks. Phishing is a generic term for email attacks that cybercriminals use to collect sensitive data in messages that appear to be from legitimate or trusted senders. Typically, the destination page is themed to represent a well-known website to build trust in the user.
Techniques used in Attack simulation training
Microsoft has provided several phishing techniques that you can use to check the vulnerability of your users. Different payloads are available for different techniques. The Payload is the content of the attack. It contains phishing messages, webpages, and malicious URLs sent to users.
Here are the available social engineering techniques:
-
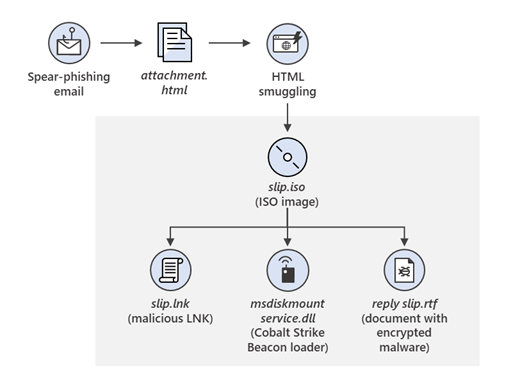
Credential harvest and links in attachments.
This technique is widely used by attackers to illegally obtain employees’ login information. By clicking on the URL, the user is taken to a website where attackers simply ask for the victim`s credentials. -
Malware attachment.
Designed as documents, voicemails, or PDFs, malicious email attachments opened by the recipient, allow attackers to install additional code or further entrench themselves. -
Links to malware.
This technique is widely used by attackers to illegally obtain employees’ login information. By clicking on the URL, the user is taken to a website where attackers simply ask for the victim`s credentials. -
Drive-by-URL.
Attackers use this fileless infection technique to download the background code on users` devices to steal their credentials and expose users to different types of threats.
How to launch simulated attacks in your tenant?
Your organization should have Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2 subscriptions to run the Attack simulation training in the Microsoft 365 Defender portal. You can launch Attack simulation training immediately or schedule it for a specific time. It is always better to plan the simulations well in advance and then schedule them for specific groups on certain dates.
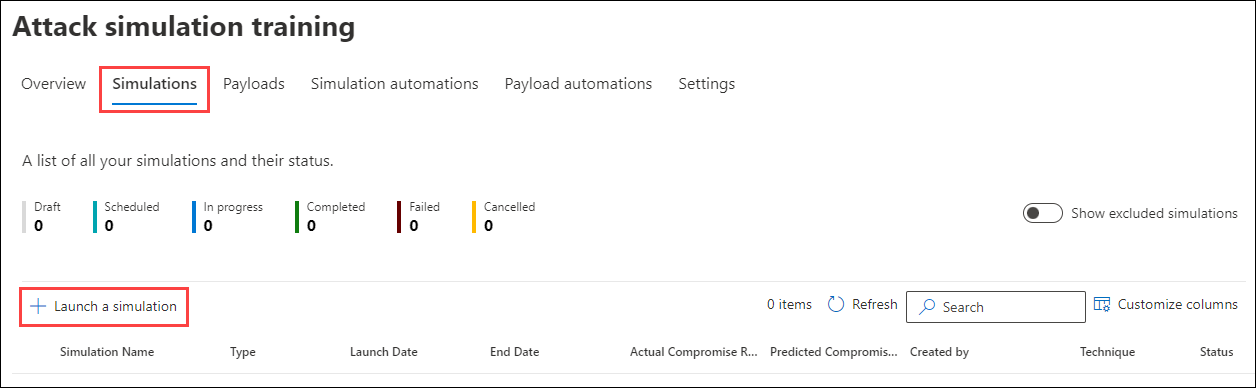
To launch a simulated phishing attack, do the following steps:
-
In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & collaboration > Attack simulation training > Simulations tab.
-
To go directly to the Simulations tab, use https://security.microsoft.com/attacksimulator?viewid=simulation.
-
On the Simulations tab, select Launch a simulation icon.
Phishing attacks have become sophisticated, harder to detect, and easier for cybercriminals to create and deploy. Therefore, it is essential for organizations to train their employees against potential cyber-attacks. Attack simulation training helps you test your security policies and practices and train your employees to increase their awareness and decrease their susceptibility to attacks.
Share
2022-06-24