Prevent security breaches with Microsoft Defender for Endpoint
Security is one of the biggest challenges that modern businesses face. Recently, many organizations have suffered various cyberattacks that have revealed tons of confidential data. These attacks have become much more complex, and it can take several months to detect the intrusion in the network.
Microsoft offers Microsoft Defender for Endpoint (previously called Microsoft Defender Advanced Threat Protection), to help you increase cyber security awareness. It is an enterprise endpoint security platform designed to prevent, identify, analyze, and respond to advanced threats.
Microsoft Defender for Endpoint continuously checks the network for malicious activity using the following combination of technology built into Windows 10 and robust cloud services:
- Behavior sensors: built-in sensors gather and process behavioral signals from the operating system. The sensor data is sent to your private, isolated, cloud instance of Microsoft Defender for Endpoint.
- Cloud security analytics: big-data and unique Microsoft optics analyze the information received from the sensors and allow behavioral signals to translate into insights, detections, and recommended responses to advanced threats.
- Threat intelligence: Microsoft security team together with partners provide threat intelligence to enable Defender for Endpoint to discover attacker tools, techniques and generate alerts when they are observed in collected sensor data.
Defender for Endpoint includes a wide range of capabilities:
Threat and Vulnerability Management
This embedded capability uses a risk-based approach to discover, prioritize, and remediate endpoint vulnerabilities and misconfigurations in real-time.
Attack surface reduction
This set of capabilities apply proper configuration settings and mitigation techniques to eliminate risks and minimize the vulnerable areas of your organization. Attack Surface reduction also provides network protection and web protection to help you manage access to malicious IP addresses, domains, and URLs.
Next-generation protection
Microsoft Defender for Endpoint uses next-generation protection to block sophisticated attacks and all types of emerging threats, including never-seen-before polymorphic/metamorphic malware and fileless/file-based threats.
Endpoint detection and response
Endpoint detection and response capabilities are used to recognize attacks using behavioral analytics and machine learning. Advanced hunting offers a threat-hunting tool that allows you to discover breaches and create custom detections.
Automated investigation and remediation
This feature helps organizations reduce the volume of alerts in minutes. It automatically analyzes them and applies artificial intelligence to determine if it is really a threat in order to decide what actions to take. This functionality allows IT departments to concentrate on more strategic tasks for the company.
Microsoft Threat Experts
This new managed threat hunting service provides proactive hunting, prioritization, and additional context and insights that further empower Security operation centers (SOCs) to discover and respond to threats quickly and accurately.
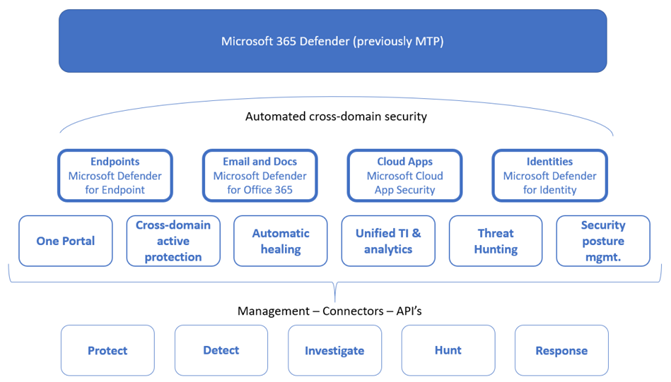
Microsoft 365 Defender
Microsoft 365 Defender protects your organization against malicious threats posed by email messages, links (URLs) and collaboration tools. It uses extensive machine learning models to block impersonation attempts and mitigate the risks. Integration with Microsoft solutions
Defender for Endpoint directly integrates with various Microsoft solutions, including:
- Azure Security Center: provides you with the tools to strengthen your network, secure your services and make sure you're on top of your security posture.
- Azure Sentinel: delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
- Intune: enables people in your organization to be productive on all of their devices, while keeping your organization’s information protected with policies you create.
- Microsoft Cloud App Security: provides great visibility, control over data travel, and advanced analytics to detect and combat cyberthreats across all your Microsoft and third-party cloud services.
- Microsoft Defender for Identity: monitors and analyzes user activities and information across your network, such as permissions and group membership, creating a behavioral baseline for each user.
- Microsoft Defender for Office: safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
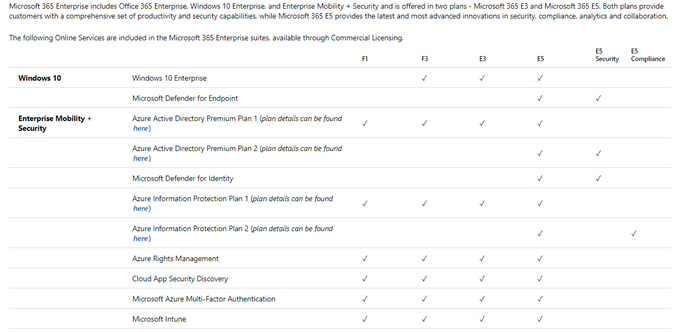
Eligible licensed users may use Microsoft Defender for Endpoint on up to five devices. Microsoft Defender for Endpoint requires one of the following Microsoft volume licensing offers and is also available for purchase from a Cloud Solution Provider (CSP):
- Windows 10 Enterprise E5
- Windows 10 Education A5
- Microsoft 365 E5 (M365 E5) which includes Windows 10 Enterprise E5
- Microsoft 365 A5 (M365 A5)
- Microsoft 365 E5 Security
- Microsoft 365 A5 Security
- Microsoft Defender for Endpoint standalone
For servers:
- Connecting servers to Azure Security Center
- Microsoft Defender for Endpoint License for Servers (one per covered server).
Microsoft Defender for Endpoint is a cloud delivered endpoint security solution that offers powerful tools to keep your company secure, leveraging it to a maximum level of protection.
Share
2021-04-02