Microsoft 365 Phishing Attacks
Phishing has been around for nearly as long as email has. More than 90% of organizations report being hit by targeted email attacks, with 23% suffering financial damage that can average $1.6 million and up. More businesses than ever are now choosing to use cloud services. But cybersecurity remains a critical issue for all businesses, as cybercrime hasn't been stopped by the cloud. Microsoft offers modern, complex anti-phishing tools that keep your employees safe from targeted phishing campaigns.
Microsoft 365 phishing attacks are on the rise
Microsoft 365 has gained in popularity among hackers for the past few years. M365 is a multisystem workspace with lots of sensitive information. Administrators can manage credentials across various Microsoft 365 services, such as OneDrive, Skype, SharePoint, and Office Store, turning Microsoft 365 into a treasure trove for attackers. Phishing is no longer just an email problem. A lot of employees keep their company's confidential information in SharePoint, which can cause great harm in case of its exposure.
Why we keep taking the bait
With M365 credentials, a hijacker can easily manage phishing campaigns from within the company. Attackers simply collect more sensitive data and extend it across other companies, as well as gain account access to get a payoff. Employees can configure filters, back-end rules, and policies to combat the inevitable exposure email provides, but overall, they have little control over what comes into their inbox, and phishing campaigns are getting trickier all the time. Hackers imitate the look of M365 messages and interfaces to mislead your staff members and trick them into their login and password disclosure. Sometimes, phishers use Microsoft Azure Binary Large Object (BLOB) storage to create landing pages with Microsoft-signed SSL certificates and a windows.net domain and perform attacks right from Microsoft 365. The malicious emails come from legitimate accounts and this can go unrecognized, simply because attackers are collecting data while logged in using authorized credentials.
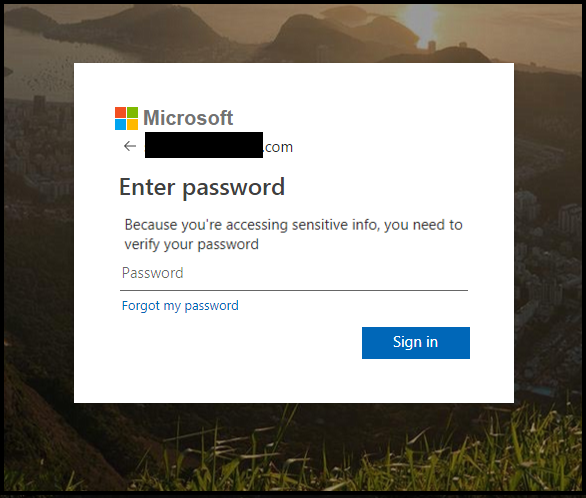
Current Microsoft 365 attack types
M365 scams are getting much more sophisticated, with a unique sender/IP, URL, and subject line for each message. These campaigns pretend to be from Microsoft 365 and start with an email indicating that you have missed a call and have received a voicemail. The message has a link or an attached HTML file that redirects the user to a phishing site created to steal your M365 login credentials. To keep yourself protected in such phishing attacks, you should always examine thoroughly the URLs of any landing pages with Microsoft login forms. Another good idea is to use multi-factor authentication, as well as different passwords for various services. It is very important to be more cautious than ever when opening attachments from unknown senders.
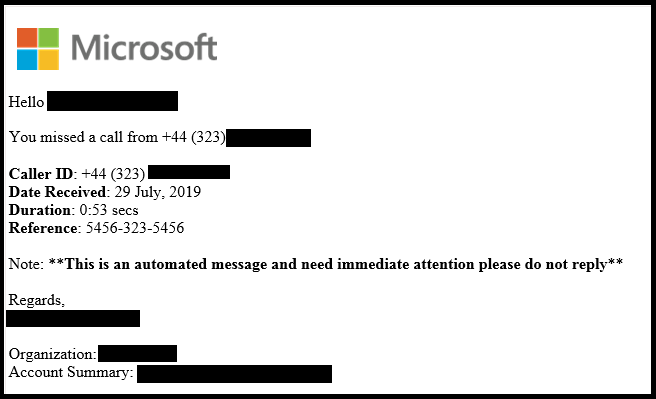
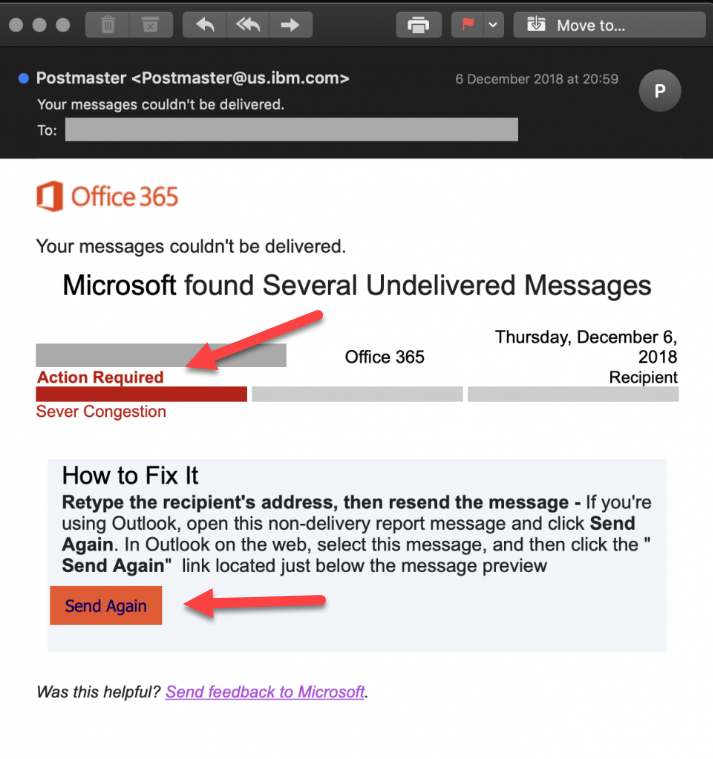
Hacking is becoming increasingly profitable and scammers' software is getting more complex. Smart campaigns anticipate the spoof messages users may normally receive. The messages with a subject line "Actions required" contain a link mainly hosted on a legitimate although hacked website to trick reputation-based email filtering systems. This is the way hijackers harvest your sensitive information and use the compromised Microsoft 365 account to perform cyberattacks within your company.
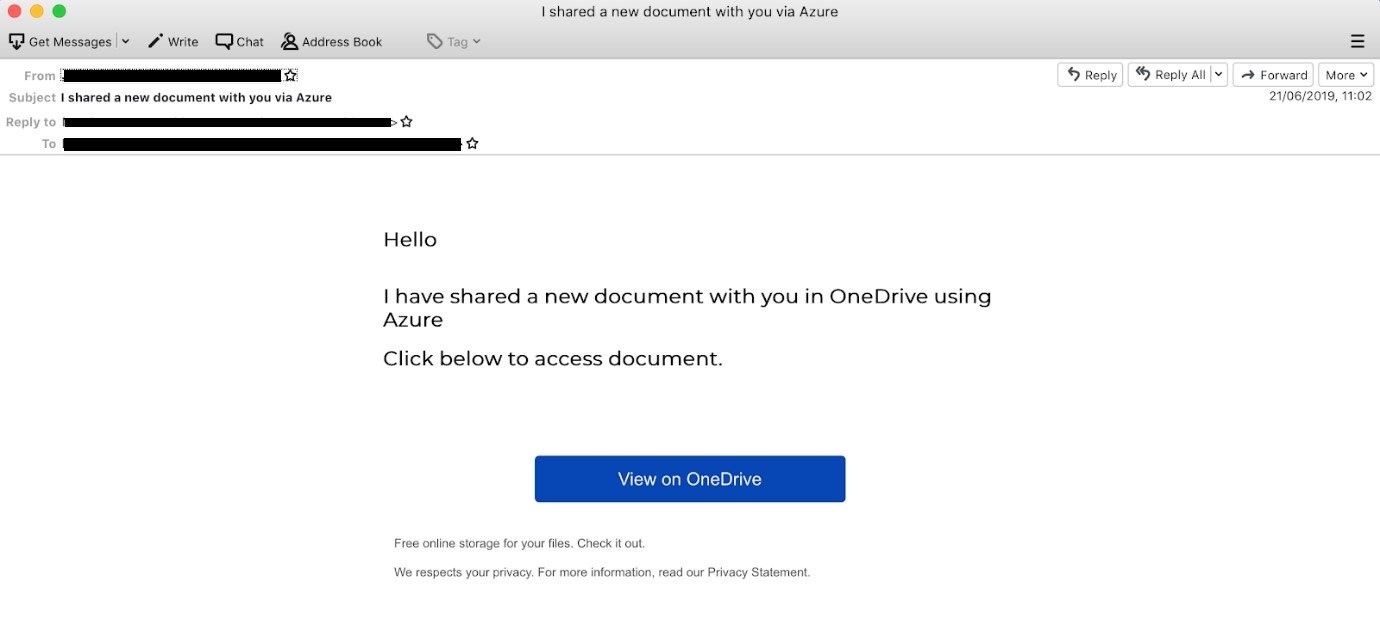
Another popular type of attack concerns the file-sharing part of M365. You can receive a fake email with SharePoint documents or an email with some file-sharing notification that will redirect you to an imitated OneDrive login page. Malicious links allow phishing attackers to bypass the built-in security of the platform and harvest your account credentials.
How to prevent Microsoft 365 phishing attacks
Microsoft 365 provides a broad range of benefits for business email, but it becomes more challenging to identify Microsoft 365 phishing scams, as they have significantly increased in sophistication and can easily bypass most security countermeasures. Phishing campaigns are a persistent danger to all businesses, and there are a few ways to risk mitigation when it concerns M365 phishing scams.
One of these approaches is user awareness training. According to the research, 52% of users receive training no more than twice a year, and 6% of users have never received security awareness training. Most employees aren't trained to detect phishing attempts, and as a result, they become an easy target for hackers by clicking on the links or opening attachments in emails without considering possible serious consequences. The more aware your employees are, the more likely they will be able to recognize a phishing attempt.
Another way to lower the chances of your organization falling victim to phishing scams is to add an additional security layer through an API to complement Microsoft's Exchange Online Protection (EOP). Using multiple anti-malware engines, it performs an advanced, complex, real-time analysis to defend your company from unknown cybersecurity threats. Embedded AI technologies identify new attack methods by analyzing uncommon behaviors in the way emails are framed and sent.
To protect sensitive information in your organization, you should be aware of the strategies that cybercriminals use to target your business. Make sure your employees are well-informed about various possible phishing attacks and know how to detect danger and protect their confidential data. A cyberattack is just a matter of time, and being able to identify a threat early on and take actions on it can significantly mitigate its impact.
IT Partner provides a wide range of tools to improve security in Microsoft 365 and help with implementation of anti-phishing options. With IT Partner's comprehensive services, IT Teams can easily train staff members on cybersecurity and neutralize Microsoft 365 phishing scams and other threats.
Share
2019-11-12