Microsoft Threat Protection
#advanced threat protection, #cloud security, #modern security
Microsoft Threat Protection offers brand-new threat information in real time, viewed in an updated UI. It is very crucial for the Security Team to access threat information immediately, as well as identify and resolve the latest impact of those threats to the enterprise.
User-reported phish
The Automated Incident Response (AIR) functionality helps enhance the admin experience. Threat information updates right away, providing the latest threat details across your environment.
There can be thousands or tens of thousands of phish emails in your environment each day. It is a daunting and time-consuming task if a SecOps team tries to deal with each one of those emails as single alerts. AIR takes the bulk of these alerts and investigates and provides actionable recommendations, making the SecOp's day-to-day life easier. Microsoft Threat Protection AIR is also designed for security readers to have access to the automated investigations as well.
SecOps engineers can use the Microsoft 365 Security & Compliance portal, and then navigate to the Alerts dashboard. Microsoft has made it simple to navigate to the alert page and examine the alerts directly. The Report Message add-in for Outlook and Outlook on the web enables people to easily report suspicious email, whether safe or malicious, to Microsoft for analysis. This information surfaces in the Security Dashboard and other reports. The organization uses these submissions to review and update security policies.
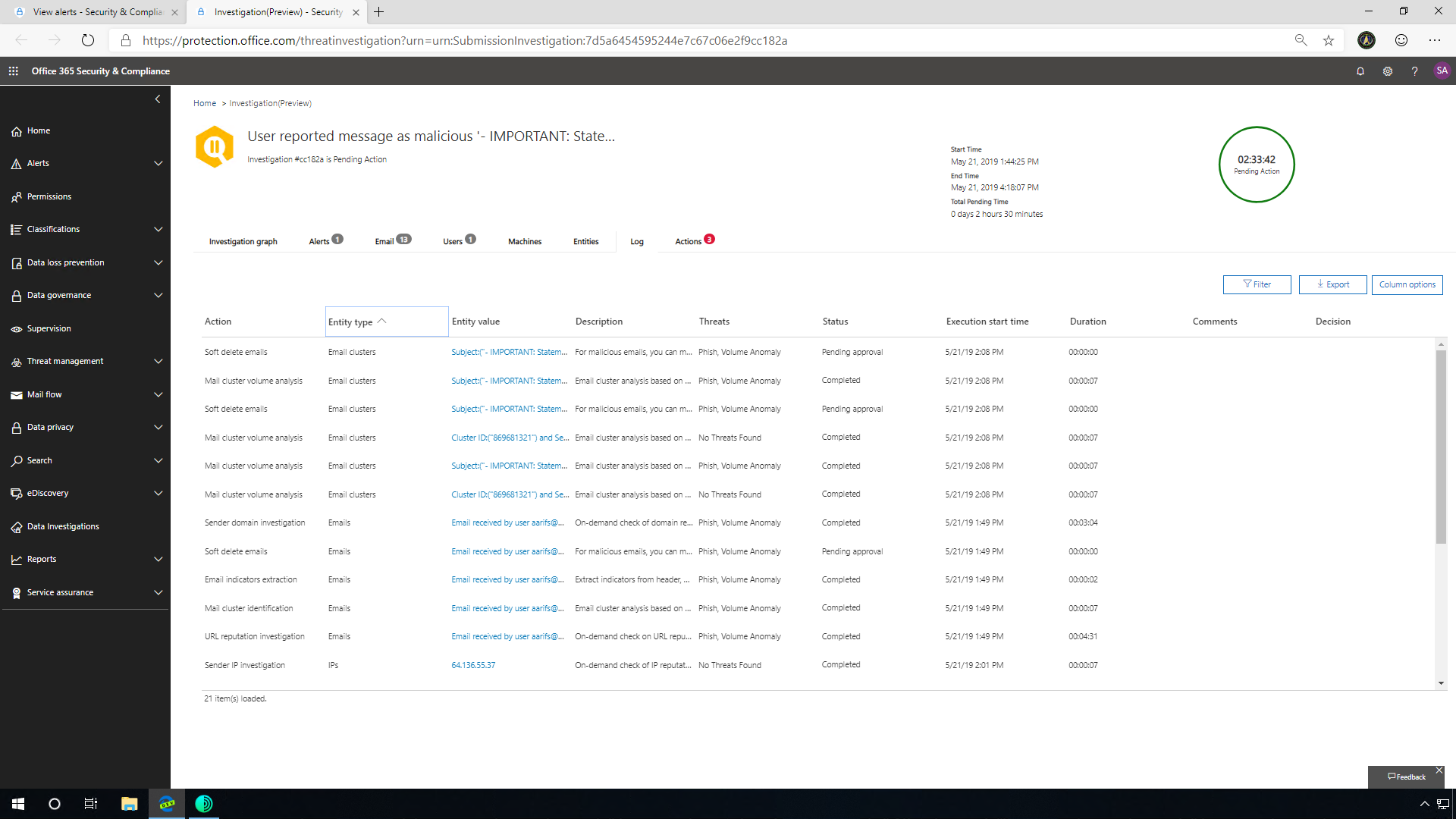
The system can investigate several different items based on one email. It is possible to re-sort by entity type so you can see the different pieces that it's been looking at from the email. The Microsoft Threat Protection engine analyzes a massive number of emails and groups them based on similarities. They may contain the same content, subject, or come from the same IP address. AIR analyzes the URLs, the IPs, as well as the sending domain. With this built-in intelligence, even if the attacker happens to have changed the sender address, changed the subjects of the emails, or changed the sending infrastructure, AIR is still able to find those bad URLs in the environment.
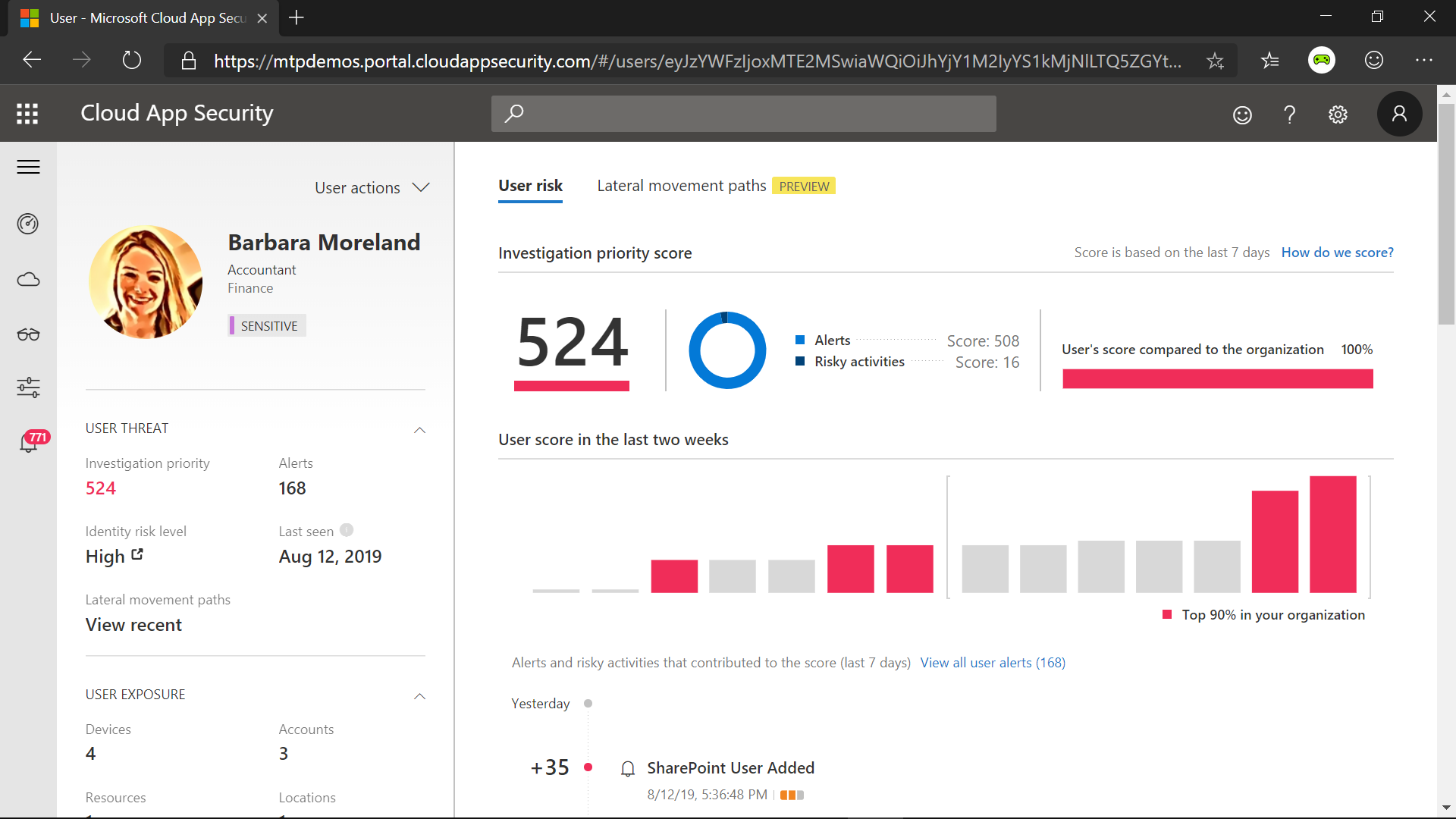
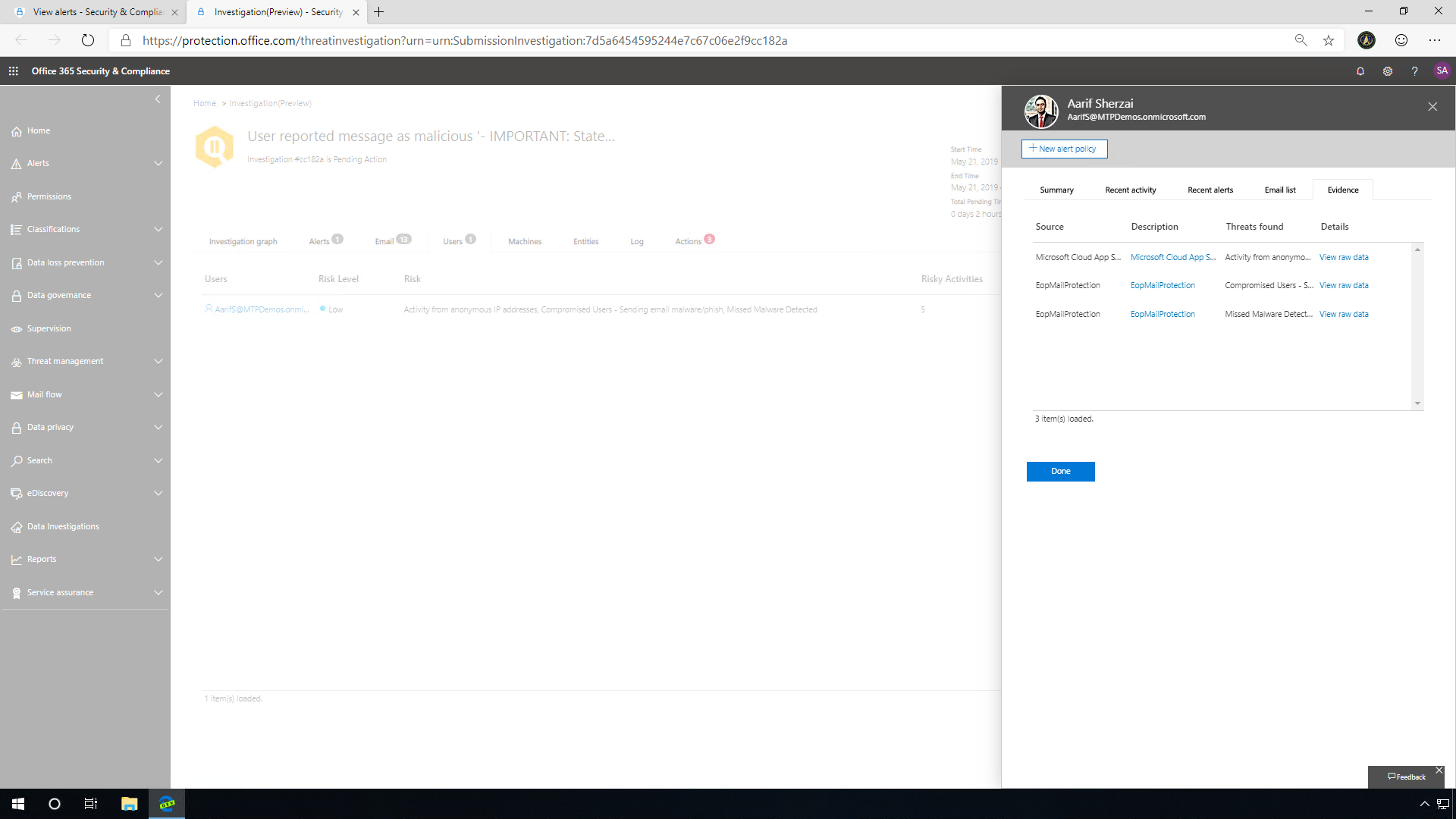
AIR also analyzes the users. If the system identifies a malicious URL click associated with the user, you can click into the evidence tab to find out more about this user. This will give you context about who they are and what's been going on with them recently within Microsoft 365. SecOps should follow up with this user and investigate further. This integration of Microsoft 365 Advanced Threat Protection with MCAS helps provide an organization extensive visibility into the threat landscape. This comprehensive protection is a key differentiator for Microsoft Threat Protection.
Clicked URL verdict changed to malicious
URL verdict changes are a simple and easy way for malicious content to make its way into a company. A simple innocuous link can be changed post-delivery to a site or file that the end user was not expecting.
SecOps get "A potentially malicious URL click was detected" alerts from a different system. But for ease, Microsoft has made it simple to navigate to the alert page and explore the alerts directly. The investigation graph breaks down the incident and includes all the actions and objects associated with the particular incident. After the investigation starts, it's going to analyze that particular email where the malicious URL was identified, then start to investigate following a series of defined steps. These steps include looking at the emails that may be related to this, as well as the user, and any machines that may be affected by leveraging Microsoft Defender ATP integration.
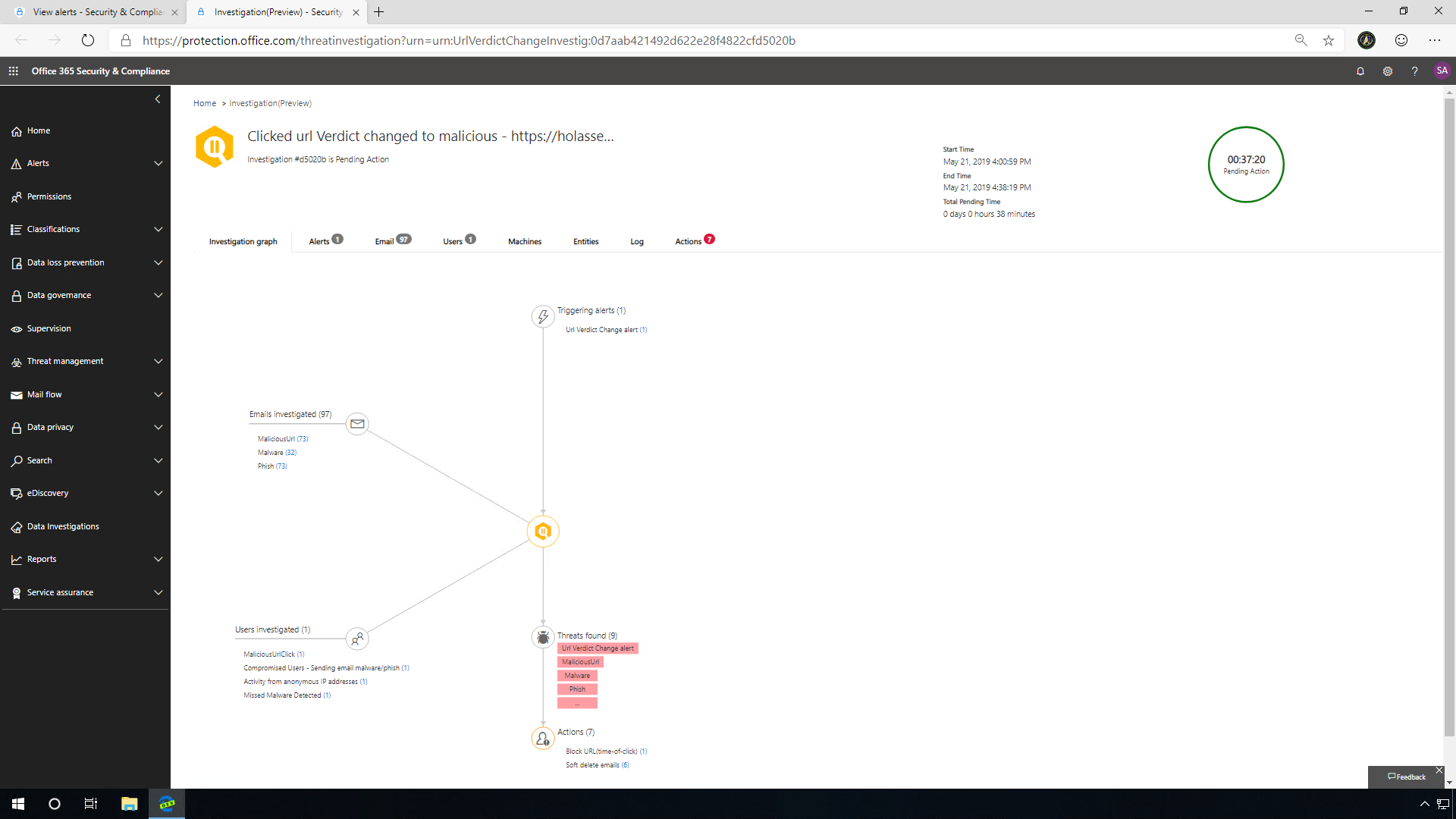
SecOps can easily follow up directly with the user who has performed some risky user behavior and investigate further, because perhaps this action was not the real user at all. This integration of Microsoft 365 ATP with MCAS helps provide customers an extensive visibility into the threat landscape. This comprehensive, integrated protection is a differentiator for MTP.
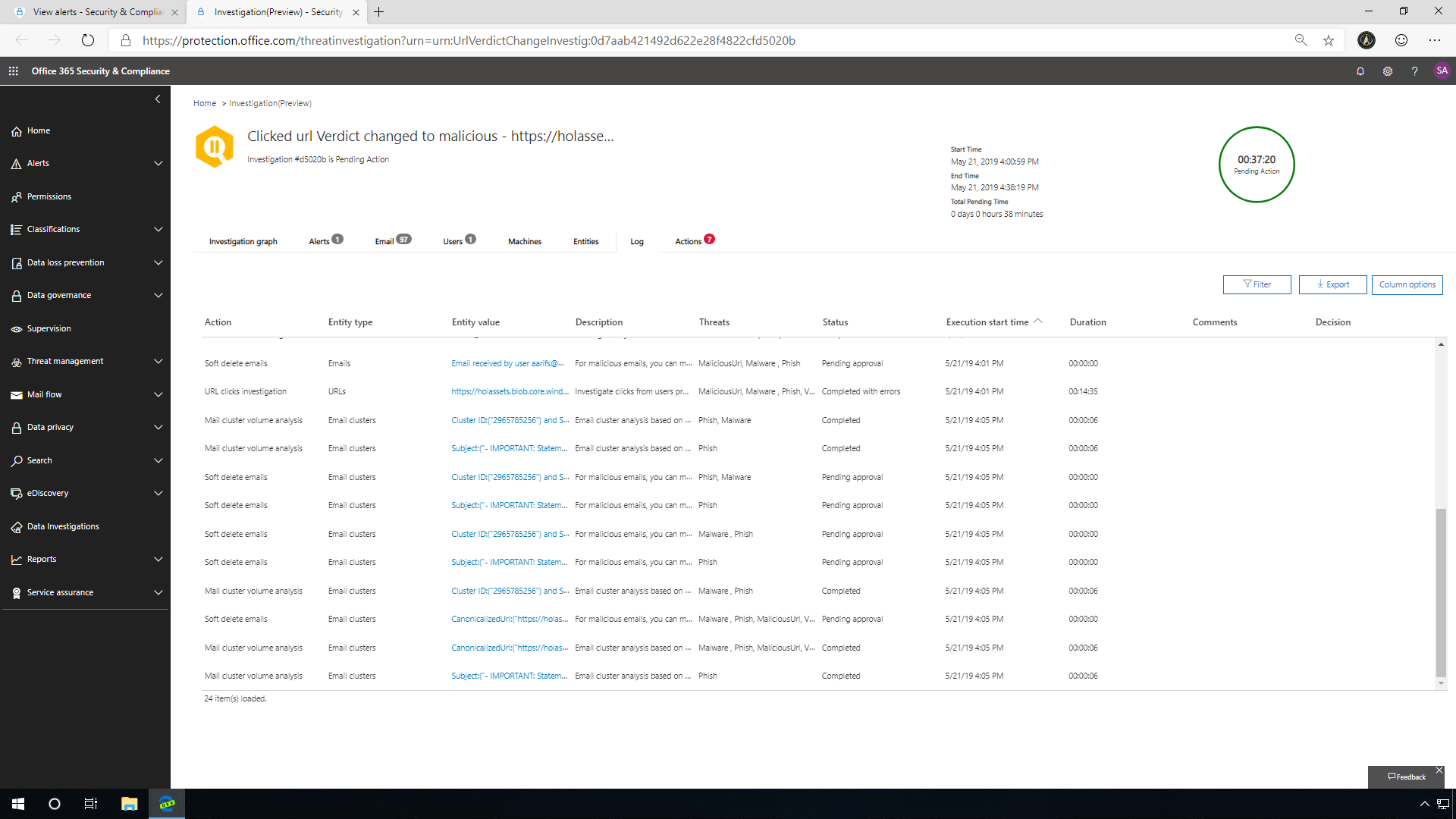
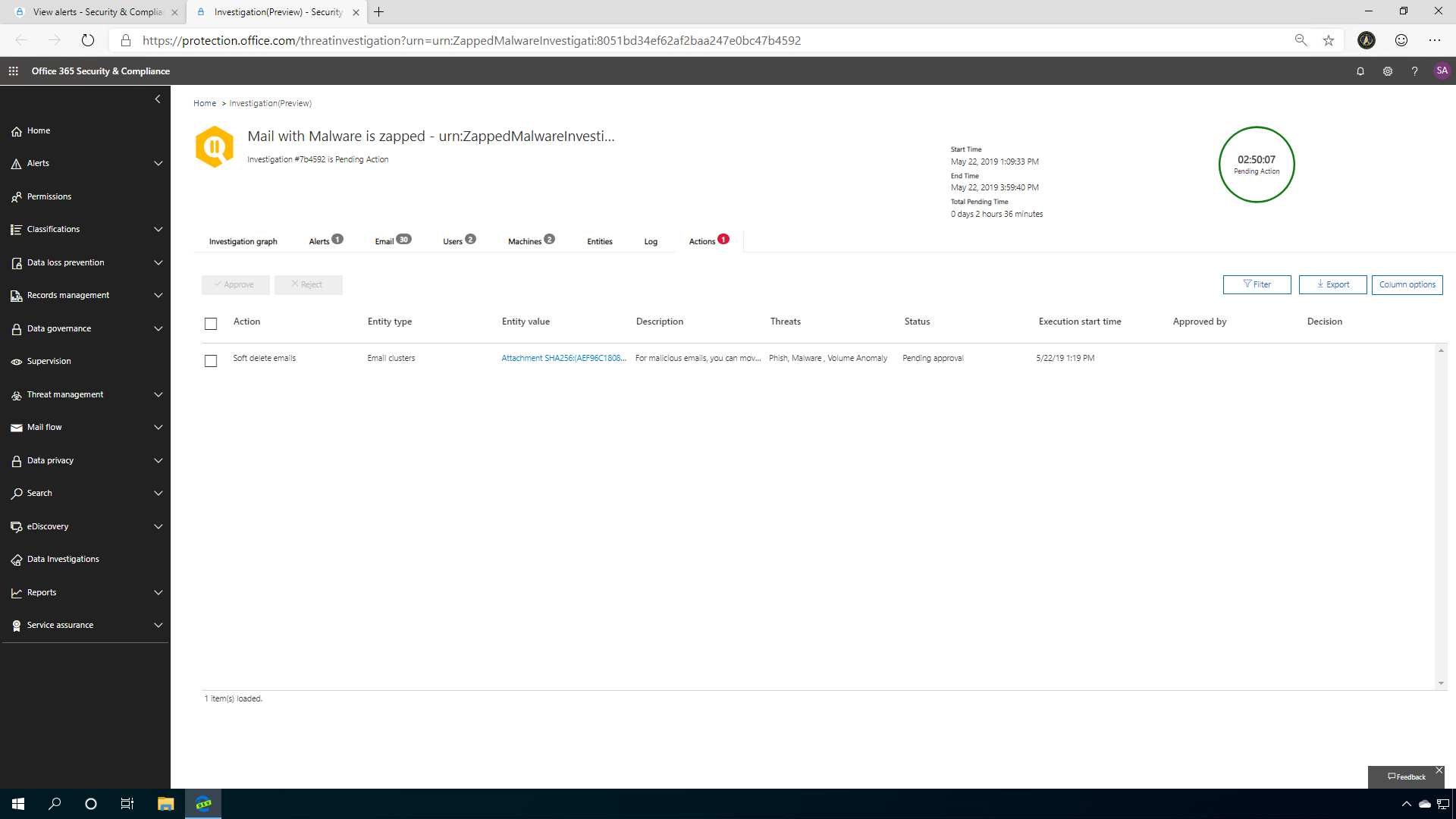
The Logs tab provides you with a breakdown of the incident as a detailed timeline of events: from the initial click, identification of the URL verdict change, user investigation, all the way to the recommended actions. Here you can truly follow the process that AIR took while investigating the incident. Clicking into these entities will open the AIR explorer, and from there you can get more information on each item.
MTP with Automatic Investigation and Response allows Security teams to quickly examine and respond to threats to protect their organizations from harmful activities, as well as identify potential threats and proactively respond to them to discourage risky user behavior.
Zero-hour auto purge investigation
Zero-hour auto purge helps to remove the infected messages from your Microsoft 365 mailboxes.
In the email tab, all the emails are clustered by the type, as well as similar files, such as attachments including relevant threats (malware, phish). If you want more details, click back on the email cluster details tab. From the explorer page, you can view similar items in email, including Sender(s), Subject(s), as well as the Body of the messages, all matching the fingerprint of the original alert.
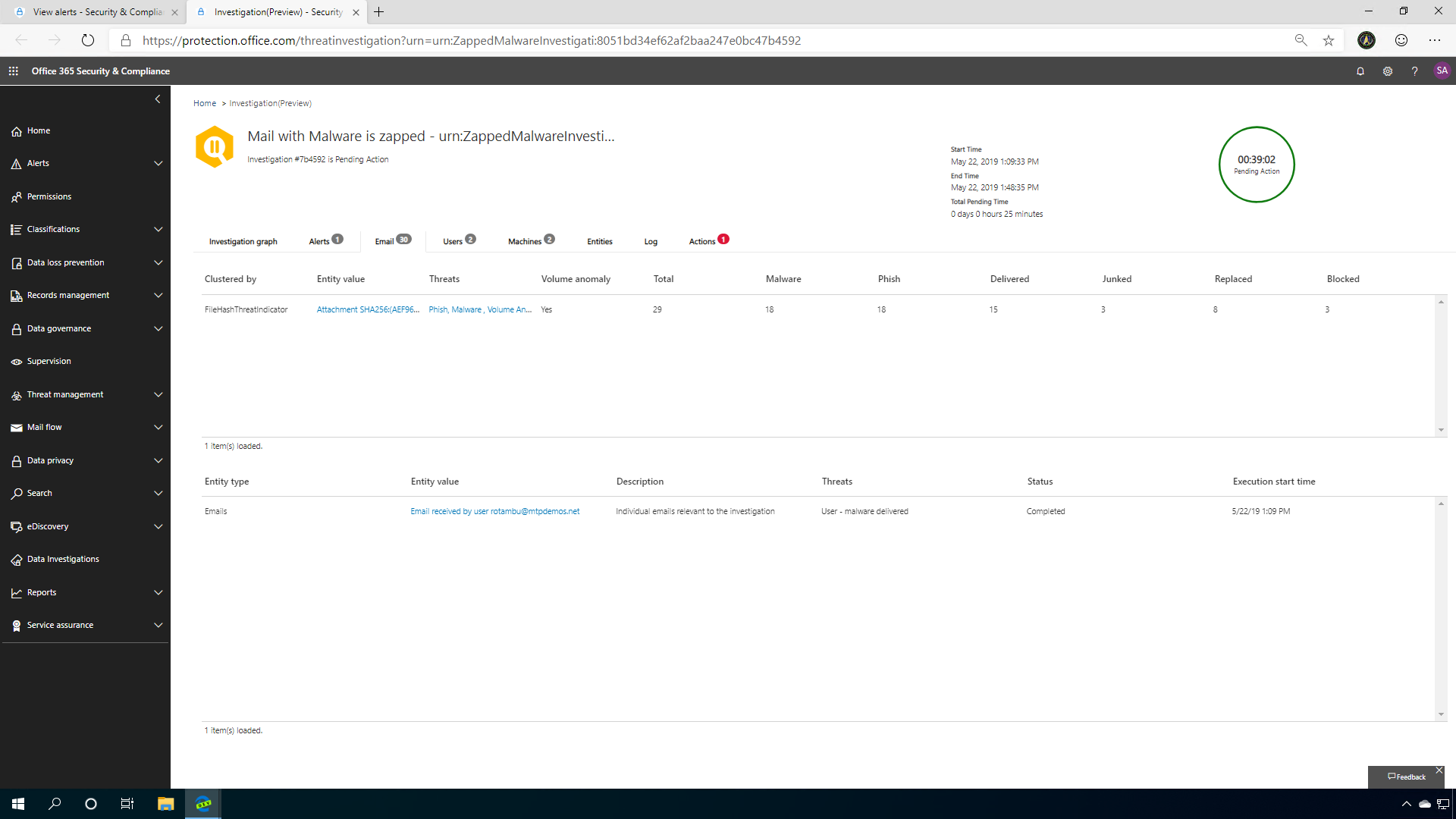
You can also identify if there were any malicious URLs within the zapped mail and if anyone clicked on them and see the origin of the email in a map view.
Clicking on the user's tab, you will find the originally targeted user, as well as a risk assessment of that user. By clicking on that user, and then on the Evidence tab, you can analyze the relevant user activities and risks identified across audit logs, Exchange Online Protection, and Microsoft Cloud App Security.
Clicking on the Machine tab lets you see how Microsoft Defender ATP integration with MTP AIR can really secure your company and help you identify the threat on your machine.
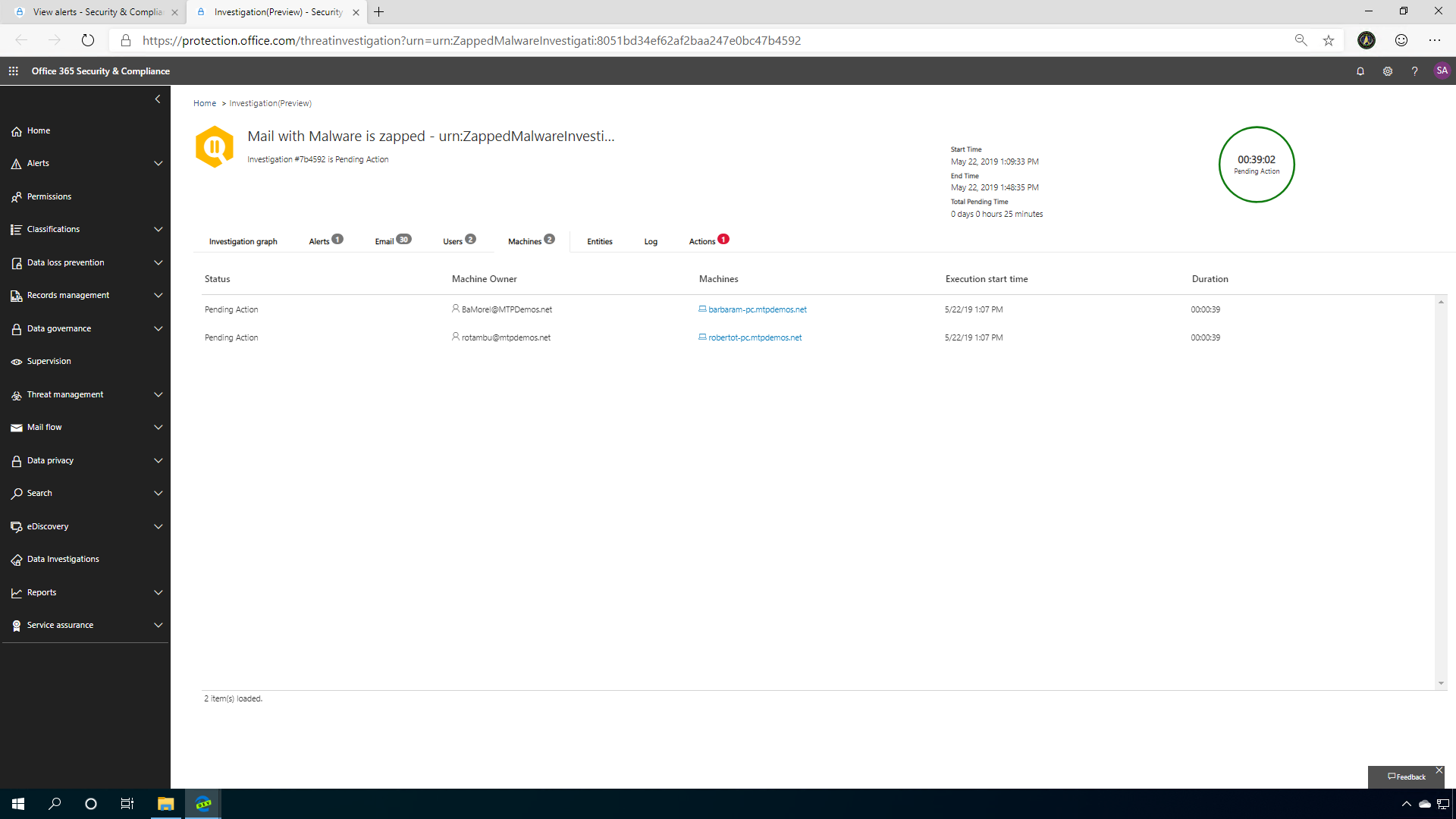
You can always head back to the incident alert to see what Microsoft Defender ATP AIR has discovered about the incident. MTP AIR is deep-linked into Microsoft Defender ATP investigations on machines that are Azure AD or Hybrid Azure AD joined and enrolled in Microsoft Defender ATP services. This takes advantage of the policies based on Microsoft ATP alerts and investigations. This "signal/information sharing" between Office ATP and Microsoft Defender ATP allows this integration to happen, and to happen automatically when a zero-hour malware is detected and zapped.
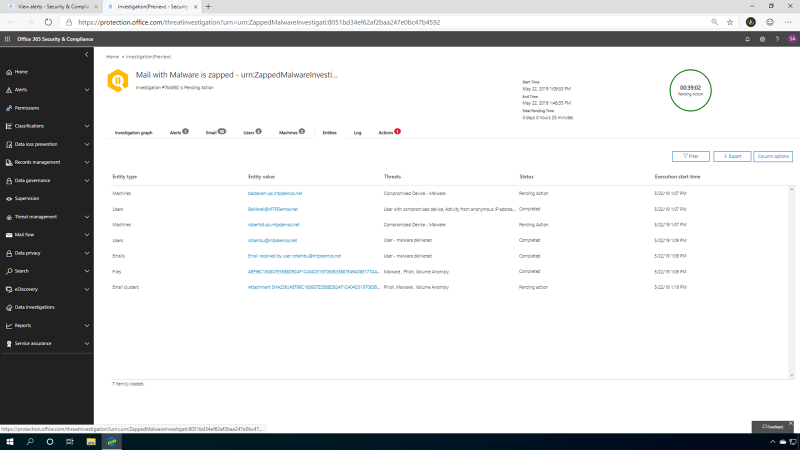
Clicking the entities tab on the investigation page helps you find all the objects that were involved in the incident. You can see the machines, users, emails, files, and email clusters all centrally located in this section. The Action tab provides a list of recommended actions for SecOps to contain and mitigate threats in the analysis.
Microsoft Threat Protection gives SecOps teams an opportunity to explore incidents faster, easier, and protect your endpoints more securely.
Share
2020-01-21