Microsoft 365 Security: Exploring Attack Scenarios
#cloud app security, #cloud security, #security
Microsoft 365 Security is smart. It’s constantly learning. New capabilities are being added. The user experience is evolving. These facts make creating a perfectly consistent CIE experience challenging. Alerts created to support the story represented in the click-steps may not consistently show up.
Microsoft tried their best to outline the most consistent path but knows that over time, things may change. That's not a negative -- it's a positive talking point to your audience if an expected part of the experience doesn't show up -- it's Microsoft 365 Security automatically responding to potential threats.
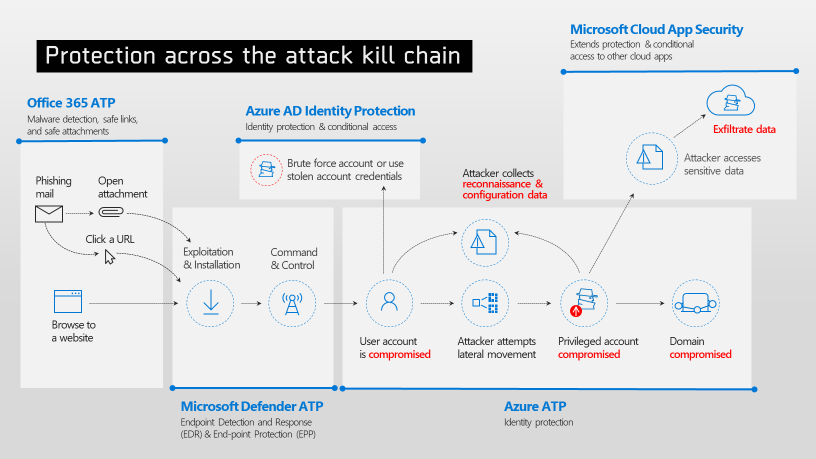
Microsoft 365 Security Center helps you manage your security posture.
The info spans across user risk, device compliance, data leakage
prevention policy matches, infrastructure protection, and discovered
cloud apps, giving you a holistic view of your complete environment.
Front and center is your secure score, a security analytics solution
that provides visibility into your company's security posture and offers
recommendations to improve your score. The overall score is a trend line
of how your score is progressing and a breakdown of the percentages of
completion across the five categories. You get a percentage and points
score based upon how well we're using security capabilities across
identity, devices, apps, and infrastructure.
In the Secure Score history area, you have several ways to interact with the details to see how improvements made recently have affected your score. The improvement actions tab offers a list of ways you can improve your score. These improvement recommendations come pre-packaged by Microsoft -- and with a simple click, you can turn on any of the improvement areas you're interested in. You can get started with the improvement by clicking on "Manage," which automatically takes you to the right admin console -- in this case, Azure AD -- Conditional Access Policies page in the Azure portal. Microsoft 365 Security & Compliance lets you filter alerts and jump into data about specific threats.
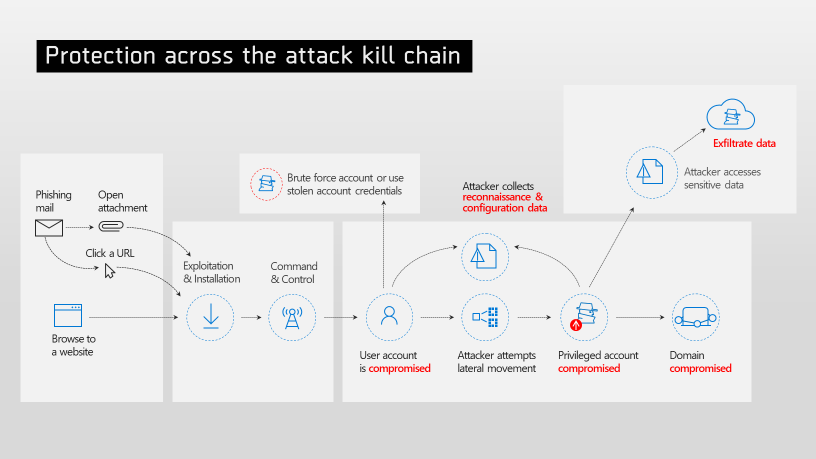
For most of us, protecting our users from email threats is job number
one -- or the one that keeps us the most preoccupied. It's also the data
breach attempt that topped the list of the 2019 Verizon Data Breach
Report -- specifically, phishing attempts. Encourage participants to
explore the investigation page -- you can point out the different
resources available to the investigation, including the investigation
graph, emails, and users being investigated, as well as the
timeframe of the threat and actions taken or required. Automated
Incident Response (or AIR) designed by Microsoft's expert
security professionals automatically contains, investigates, and
remediates today's most sophisticated threats. It is also powered by
Microsoft's Intelligent Security Graph (ISG). ISG's
purview is vast, monitoring over 6.5 trillion signals a day across
Microsoft's cloud properties.
When an external threat is identified and remediated, that knowledge is
shared -- so other organizations benefit from that knowledge. There
are two key terms to learn: incident and response. An incident is a
group of alerts associated with the same threat. Mapping out an
incident, you effectively understand the "life of the threat." You gain
insight into how it entered your environment, who and what it impacted,
and how to remove it and restore your environment to pre-threat
conditions.
Response is the containment, analysis, and remediation of an alert. Incident response is the collective response to individual alerts that form the incident. When exploring alerts manually, SecOps teams must spot and correlate entities at risk from threats. This takes too much time and implies multiple tools and systems. With AIR, you can spend less time hunting for alerts and more time focusing on preventive measures, like education and fine-tuned email security policies that best fit your needs.
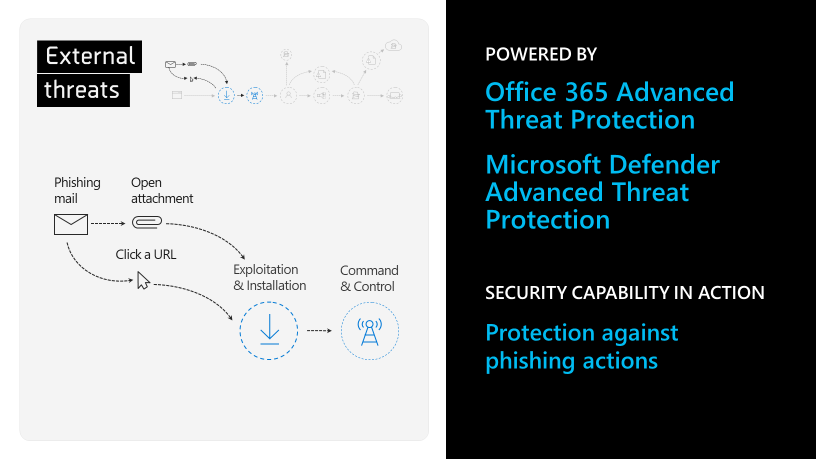
Another weapon against external threats like phishing is making your employees aware of the threats. With Attack Simulator you can easily run realistic attack scenarios in your company to recognize and detect vulnerable users before a real attack affects your bottom line. There are three kinds of attack simulations currently available: display name spear-phishing attack, password-spray attack, and brute force password attack. It is also possible to create anti-phishing policies to keep specific groups safe from phishing scams, as well as the entire domain. Microsoft security experts are seeing attackers use domain name spoofing -- to imitate emails like they're coming from known brands or colleagues. Very targeted spear-phishing has proven to be a successful approach, and more specific groups in organizations are being targeted for spoofing. Being able to provide targeted anti-phishing policies to further protect those groups is invaluable.
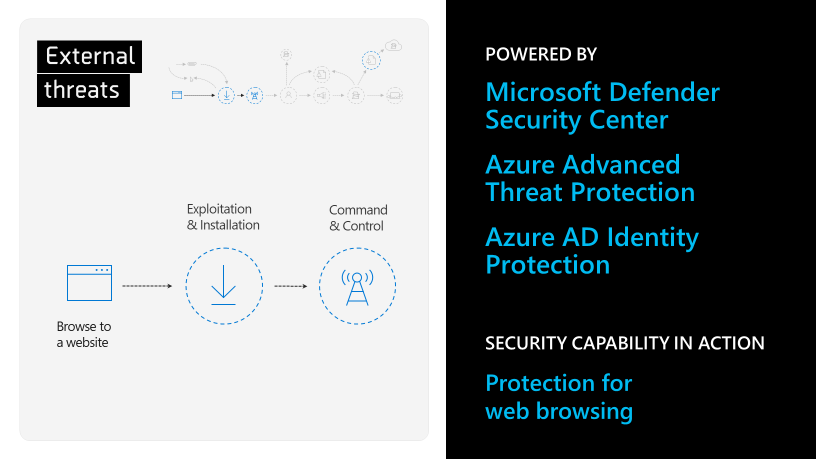
Microsoft security research is seeing a significant spike in crypto currency mining -- or crypto jacking -- where bad actors gain access to corporate resources to support mining operations. The problem with crypto jacking is that, unlike other threats like phishing, it doesn't rely on the victim to install a program that secretly mines crypto currency. In-browser crypto jacking, for example, skips that step altogether, using JavaScript on a compromised web page to get the browser to mine for crypto currencies. Hackers have used crypto currency mining as a decoy to launch more dangerous cyberattacks, and damage can also be done to the machine/device that's been "crypto jacked." And of course, crypto jacking takes resources away from systems critical to the business. To further protect the company, you can use security capabilities built into Windows 10 Enterprise and Defender to prevent employees from installing malicious and unauthorized apps. Microsoft Defender Exploit Guard is another useful tool to mitigate more sophisticated attacks.
Advanced hunting helps you identify possible threats using a powerful search and query tool. It is also possible to build custom detection rules based on the queries you created and surface alerts and benefit from shared queries from the community that are stored in GitHub.
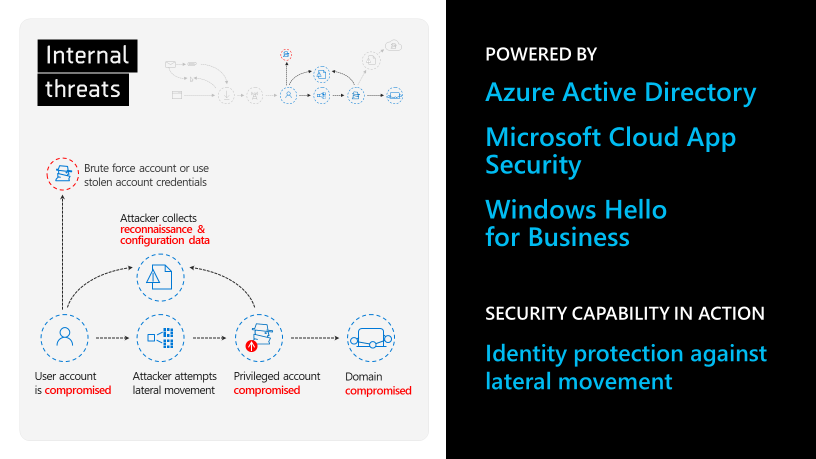
According to Verizon's 2019 Data Breach Investigation Report, 34% of breaches involved internal actors. To make matters worse, key tactics of these breaches included errors and misuse of authorized users. It's heartbreaking to think that your own employees represent a sizable cyber security threat to the company -- but it's the reality we face. You should be prepared to detect and proactively respond to these internal threats. To keep your organization's expanding universe of cloud-based apps and data safe, you need a tool that focuses on cloud app security. Microsoft 365 includes the Cloud App Security dashboard, a crucial component of the Microsoft Cloud Security stack.
Here you also have visibility into all of the apps running on the network -- and potential shadow/rogue apps in the unsanctioned apps listed. Cloud Discovery examines your traffic logs against Microsoft Cloud App Security's cloud app catalog of over 16,000 cloud apps that are impartially analyzed based on more than 70 risk factors. Each app gets a score that helps you decide whether to allow usage.
Microsoft, along with other industry leaders, is working to remove passwords using other, more secure methods. By eliminating passwords, you can reduce the odds of your identities being compromised by 99.9%, according to a recent Microsoft Security Intelligence Report -- while getting rid of the thing users hate the most -- remembering passwords! Built into Windows 10 is a passwordless solution called Windows Hello for Business, which uses biometric or a personal ID number as the method for secure sign-in. To set this up for your company, you should hop over to Microsoft Intune. There you can set the parameters of your Windows Hello setup -- whether you allow for biometric authentication, and the option for using security keys for sign-in.
In addition to Windows Hello for Business, you can also deploy Microsoft Authenticator to secure users when they are not accessing organizational resources via managed Windows 10 devices, for example, on iOS and Android.
Share
2020-02-05